How to Bypass User Account Control (UAC) in Windows 7
The User Account Control feature has been around since Windows Vista and can still be found implemented on Windows 10. Basically UAC is a security feature implemented in the Windows operating system to prevent potentially harmful programs from making changes to your computer. Even if your user account belongs to the administrators group that is supposed to have complete and unrestricted access to the computer, you are still subjected to the UAC restriction.
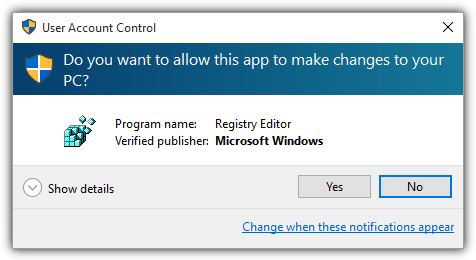
When you run an application that needs privileges to make file or registry changes that can globally affect all users on the computer, it will initiate a User Account Control notice window. The user can either click on the Yes button to allow the program that will make changes to the computer to run or else clicking No will stop it from running.
If you compare between the versions of Windows that come with and without the User Account Control feature (XP vs. Vista and newer), XP has a very high malware infection rate while the newer Windows requires a much more sophisticated and advanced rootkit malware in order to take full control of the computer. In this article we’ll be taking a closer look at how effective the User Account Control feature is and what are its weaknesses.
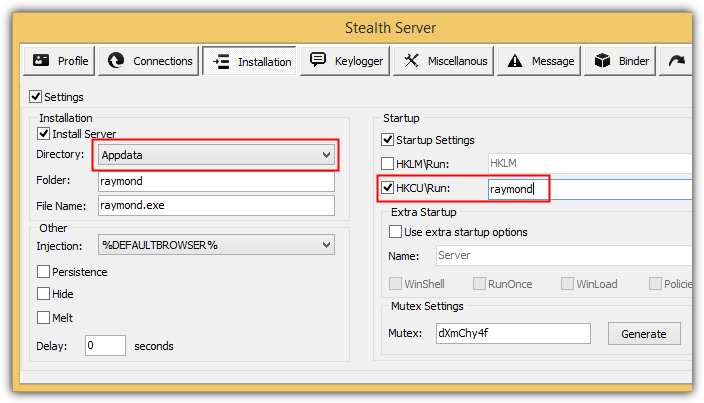
Even with UAC enabled in a system, a malicious software such as a trojan RAT can be built to install on the system without triggering the UAC notice. This is done by configuring the server builder to drop the malicious file in to user’s application data folder (%AppData%) and adding a shortcut to the user’s startup folder or a registry entry in HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run to run automatically on Windows startup.
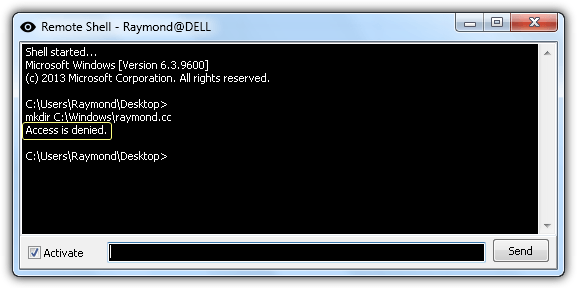
Without the UAC elevation, the malicious file only has limited privileges that can affect the currently logged in user, but not on the whole system. For example, the hacker connected to the system via a remote shell is denied from creating a new directory in Windows.
This feature that is commonly found in most RAT isn’t really worthy to be called a UAC bypass because it is just merely running silently without requesting UAC elevation that ends up with limited privileges. A real UAC bypass is when an application gains full administrative privilege through a backdoor without triggering the UAC notice and requiring the user to click the the Yes button in the UAC window.
UAC Bypass Proof of Concept
A publicly available open source proof of concept to defeat the User Account Control called UACMe can be downloaded for free from GitHub. It contains 12 different popular methods that are used by malware to bypass UAC. To test each different method of UAC bypass, simply append a number from 1 to 12 after the filename. For example:
Akagi32.exe 3
The screenshot below shows an example of using UACMe to launch a command prompt with administrative privileges without the UAC notice window.
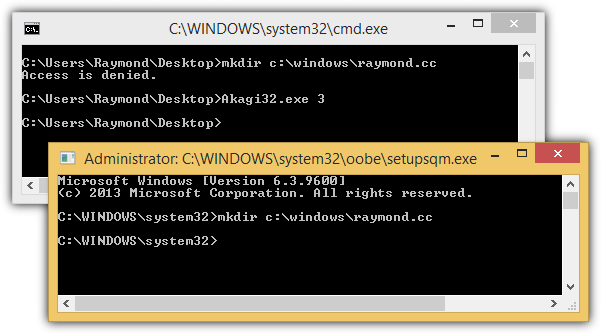
As you can see from the background command prompt window that we were not able to create a new folder in C:\Windows with the error “Access is denied”. Then we ran UACMe with method 3 and it uses a backdoor method to launch another command prompt with administrative privileges without overlaying the whole screen with a UAC warning. We were then able to create a new directory in C:\Windows using the command prompt that was launched with UACMe.
Both 32-bit and 64-bit versions are available for UACMe, so make sure you run the correct version based on the architecture of your Windows operating system.
Although it is quite rare to find a real UAC bypass feature implemented in a RAT trojan, this powerful backdoor feature can be found on some crypters that are used to make a malicious file undetectable by antivirus software. We’ve tested one of the free crypters with a “Bypass UAC” option enabled and found that the results are quite unreliable.
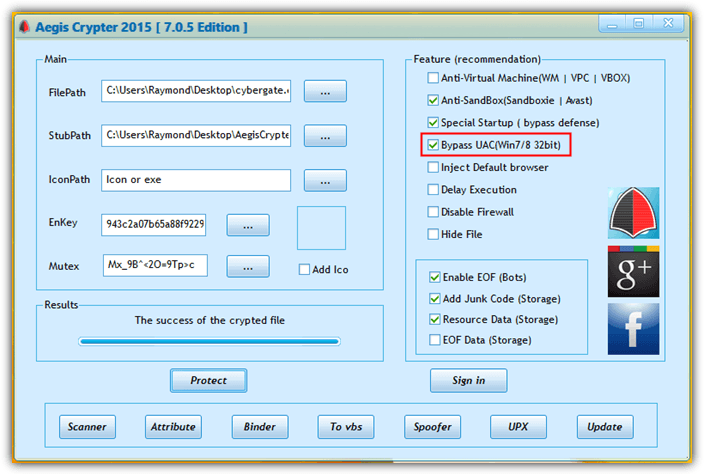
Encrypting a file with the “Bypass UAC” option enabled should give an administrative privilege to the file without the need to invoke the UAC elevation window. However some crypted files work fine while some don’t work at all.
Protecting against UAC Bypass
The default User Account Control setting which is at the third level is not safe and can be bypassed. The most effective User Account Control configuration is to set it to highest (fourth) level which is to always notify when programs try to install software or make changes to computer or to Windows settings.
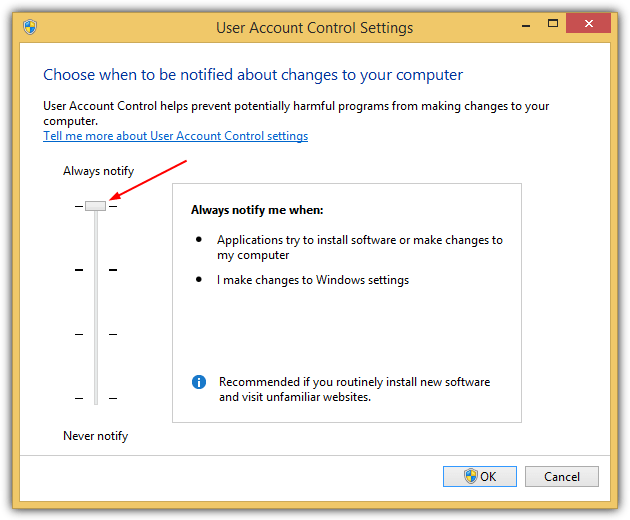
Another way is to use a standard user or guest account instead of an administrator account that is created after installing Windows.



User forum
17 messages