Learn How To Hack using Advanced Tools at Try2Hack
Most of the time computer hacking is automatically associated with computer criminals breaking into computers, servers or security systems to gain unauthorized access. However, this is not always the case because the computer security experts are also hackers except they belong to the white hat category and don’t use their skills to break the law. In order to be a hacker, one must at least know how to use the proper tools which are not normally not used by computer amateurs to harvest information which could reveal loopholes for backdoor entries. A quick way to learn how to use some of the tools is by going through the challenges provided by Try2Hack.
Try2Hack offers free challenges where you’ll start from the 1st level and completing it will bring you to the next level until you reach level 12. Each challenge requires different technique to solve and it gets harder as the level increases. We will provide the solutions and walkthrough for the levels so you can solve them if you’re stuck and also learning new skills. Click here to start the challenge!
Level 1Challenge: Enter password to continue
Solution: View the HTML source code by pressing Ctrl+U in Firefox. You will see a small javascript snippet with the password and also the location of level 2. Typing the wrong password will bring you to Disney’s website.
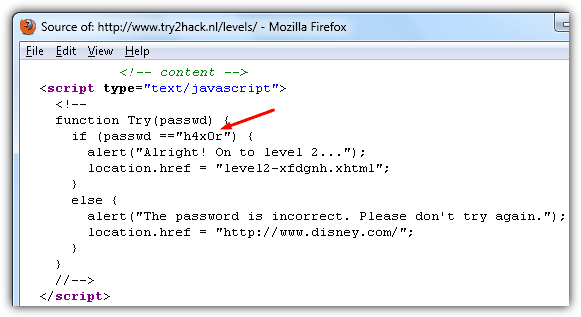
Level 2
Challenge: Enter username and password on flash based login form
Solution: View the HTML source code, and you’ll see that the login form is loaded from flash file level2.swf. Download the level2.swf and open it with Notepad. The username and password is shown in clear-text.
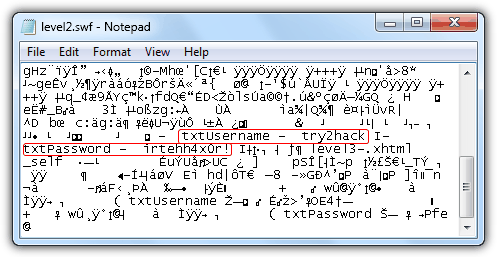
Level 3
Challenge: Enter password on a popup
Solution: This challenge contains deception in trying to trick you. View the HTML source code and open the external Javascript source file.
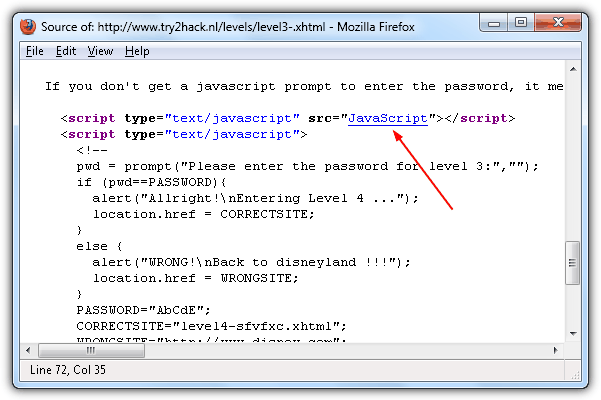
Click on the Javascript source file link to load it in the HTML code viewer and you’ll see the real password, correctsite and wrongsite values.
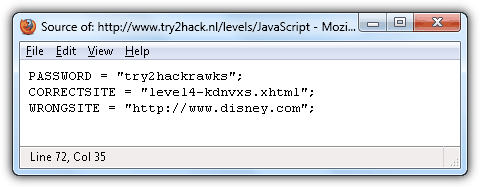
Level 4
Challenge: Login to a Java based web form
Solution: View the HTML source code, download the Java class file (PasswdLevel4.class) and decompile it with JD-GUI.
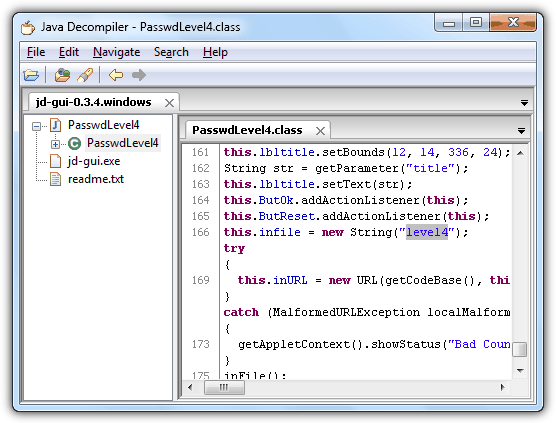
In the decompiled Java class file, it reads another external file called level4 located in http://www.try2hack.nl/levels/level4. Download the level4 file, open it with Notepad, the username, password and level 5 URL is in there.
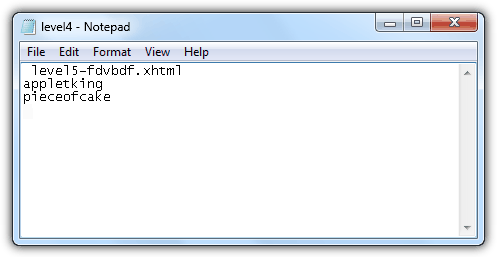
Level 5
Challenge: Enter username and password on a Visual Basic 3.0 program
Solution: Download DoDi’s VB 3.0 Discompiler. Run it, load the level5.exe file to the decompiler and wait for the process to complete. There will be a bunch of files being generated and you should only pay attention to MAIN.TXT and LEVEL5.BASE files. The username, password and the URL of level 6 is on the LEVEL5.BAS file but they are encrypted and can be easily decrypted by referring to the MAIN.TXT file. We are going to do two examples so you would understand how the username and password are calculated.
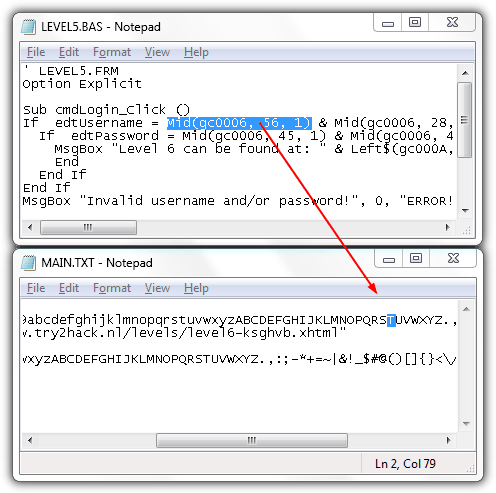
To decrypt (gc0006, 56, 1), refer to MAIN.TXT file. First, it tells you to refer to gc0006 which is the line that includes numbers, lower and uppercase letters, and symbols. Next, the number 56 represents the 56th letter on that line and the last number 1 means you should only read one character that starts from the 56th letter. The value for (gc0006, 56, 1) would be uppercase “T”. As for Mid(gc0006, 28, 1), it would be lowercase “r”.
Level 6
Challenge: Download and run a Visual Basic 6.0 program that requires to enter the correct username and password.
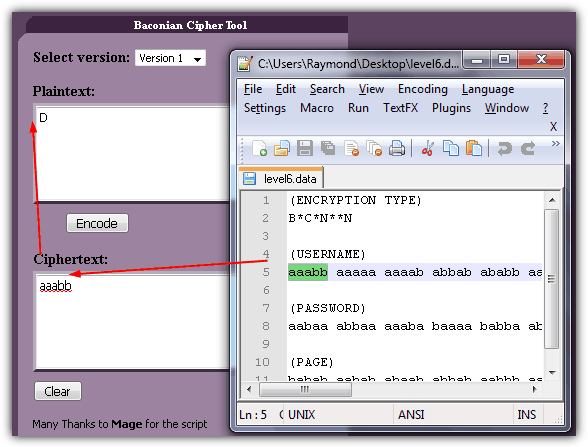
Solution: A quick test on the program will show that it connects to the Internet to authenticate the username and password that you’ve entered. The first thing you should check is to see where it connects to. Instead of using a sophisticated packet sniffing tool, you can just use URL Snooper which will reveal that the program pulls a file called level6.data at http://www.try2hack.nl/levels/level6.data.
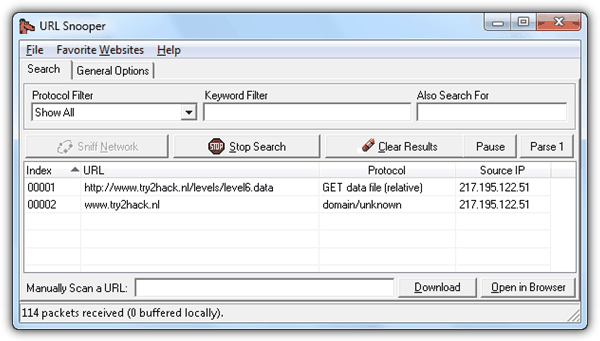
The level6.data file contains the encrypted username, password and page and we’ll have to decrypt it. It does have a hint of the encryption algorithm being used and it is BACONIAN. You can easily decrypt the BACONIAN cipher by going to this webpage, enter each blocks of ciphertext and click the Decode button. You cannot paste all of the blocks to decoded. It has to be decoded one by one.
Level 7
Challenge: Use Microsoft Internet Explorer 7.66
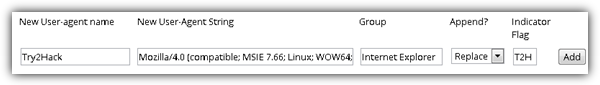
Solution: This protected page simply checks if you’re running Microsoft Internet Explorer 7.66 on Linux or Unix system and is being referred from a Microsoft page. This can easily be done by using spoofing plugins for Google Chrome. First install an extension called User-Agent Switcher for Chrome. Click on the Chrome UA Spoofer icon located at the top right and select Settings. Enter the following information and click Add.
New User-agent name: Try2Hack
New User-Agent String: Mozilla/4.0 (compatible; MSIE 7.66; Linux; WOW64; Trident/4.0; SLCC1)
Group: Internet Explorer
Append?: Replace
Indicator Flag: T2H
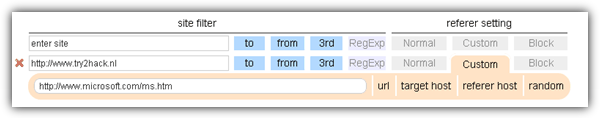
Again click on the Chrome UA Spoofer icon located at the top right, select Internet Explorer, followed by Try2Hack. If you refresh the Level 7 page, you will see OK for browser and OS check, but fail on the link check. Now install another extension called Referer Control. Right click on the Level 7 page and select “Create referer filter for this site” > “Use custom referer” > “URL”. At the highlighted box, replace the [URL] with http://www.microsoft.com/ms.htm.
Refresh the level 7 page again and a link to Level 8 will appear on the page.
Level 8
Challenge: Login form that uses CGI script
Solution: View the HTML source code and you’ll see that it submits the login information to /cgi-bin/phf. There is a very well known and old phf exploit that can be used to display the passwd file on linux system. Simply enter the URL below on your web browser and the passwd file will be displayed.
http://www.try2hack.nl/cgi-bin/phf?Qalias=3Dx%0a/bin/cat%20/etc/passwd
Again, the login information on the passwd file is encrypted but can be decrypted using John the Ripper. Download the Windows binaries version, extract it to a new folder, copy everything from the passwd file and save it to a text file. Place the text file at the same directory as John the Ripper and run the following command in command prompt. Replace the passwd.txt to the file name that you’ve used to save the content of the passwd file.
john.exe passwd.txt
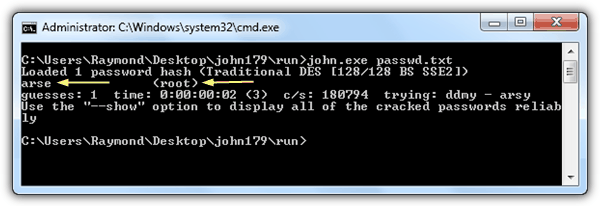
The password of the root user account is displayed which can be used to login to the level 8 web form.
Level 9
Challenge: Enter username and password on a normal looking login web form.
Solution: Everything looks normal on the level 9 login form until I started investigating on the HTTP headers using a plugin called Live HTTP headers for Firefox. It has username and password on the cookie but using the credentials to login does not work.
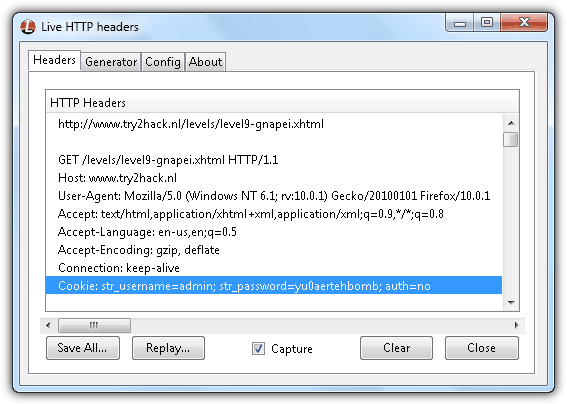
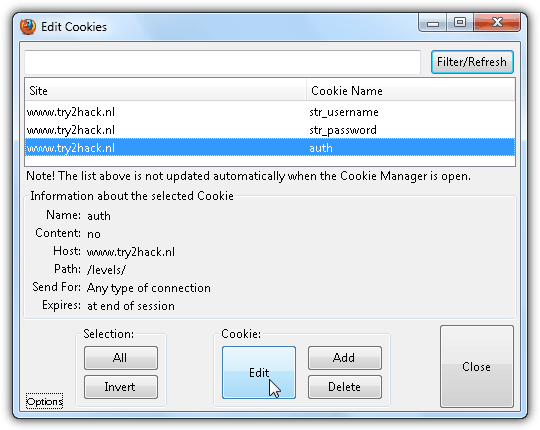
The username and password on the cookie is actually correct but there was another value that is causing it to fail which is the auth=no. All we need to do is use an extension called Edit Cookies for Firefox to change the auth=no to auth=yes. After installing the plugin, press Alt+T and select Cookie Editor from the menubar. Search for the site www.try2hack.nl with the cookie name as auth, click on it to highlight the cookie and click the Edit button.
At the content box, change from no to yes and click the Save button.
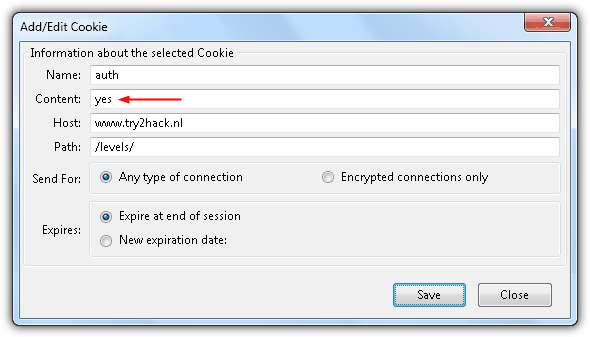
Immediately login to the Level 9 form with the username and password shown earlier using Live HTTP Headers. Do not reload or refresh the level 9 page or else you’ll need to re-edit the cookie.
The real fun about Try2Hack is trying to solve the challenges yourself by identifying the possible solutions instead of immediately looking for answers or the URL to the levels. Try them out and learn how these program works so that you can use them in future for similar situations.


My greetings and my compliments.
Followed all levels, WOW. Not because I am genius but because you done it so well.
It is the best piece of entertainment I have ever done at 3,00 am morning.
Well done
Love you web (Y)
amazing job ;) very funny stuck on lvl 5. lvl 5 file is incompatible with my windows…
Ha lol This Is Pretty Fun! Stuck On Lvl 2 lol But Wasn’t Tryin, I’ll Try Again Later