5 Packet Sniffers to Reassemble Files Uploaded or Download from FTP Protocol
The FTP protocol has been around for quite a long time and is still commonly being used today to upload files to webservers. FTP is well known to be insecure because the data is transferred in clear text which can be directly read from a packet sniffer. This would mean that the FTP login information containing the username and password can be captured by a packet sniffer when FTP client software initiates a connection to an FTP server. Encryption can be used in FTP by either using the SFTP or FTPS protocol instead of the insecure FTP.
Not only does FTP reveal the login information in clear text, the transferred files between the client and server can be intercepted and reassembled by a packet sniffer to show what files are being uploaded to or downloaded from the FTP server. This is useful for administrators to detect unauthorized transfer of company confidential files during a network traffic audit but can also be abused. Here we’ll show you 5 free packet sniffing programs that have the ability to reconstruct files that are transferred via FTP.
1. Intercepter-NGIntercepter-NG is a network toolkit that has the ability to reconstruct files transferred in FTP protocol. Other than FTP, it also support reconstruction of files from HTTP\IMAP\POP3\SMTP\SMB protocol. Other than file reconstruction, Intercepter-NG is able to sniff chat messages & passwords hashes, capture raw packets, and perform a few exploits such as Heartbleed, SMB Hijack, HTTP Injection, ARP spoofing and etc.
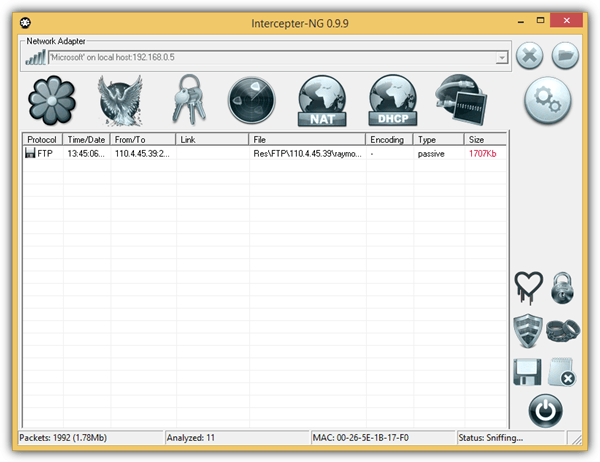
To start sniffing the network packets and reconstruct files transferred in FTP, first of all it is important to select the interface that you’ll be using to sniff by clicking on the network adapter icon located at the top left. Clicking on it will switch between Ethernet and Wi-Fi. Then click the drop down menu to select the active adapter and followed by clicking the play icon to start sniffing. Go to the “Resurrection Mode” and the reconstructed files will be listed there.
2. SoftPerfect Network Protocol Analyzer
SoftPerfect Network Protocol Analyzer is a free packet sniffer for analyzing and debugging network connections. Although it does not come with an automated way to reassemble files in the packets, we’ll show you how easy it is to reconstruct them with a few steps. The first step is to select the network interface that is currently in use to sniff the packets and click on the Start Capture button. When you’ve finished capturing the packets, click on Capture at the menubar and select Reconstruct TCP Sessions which will bring you to Data Flows tab.
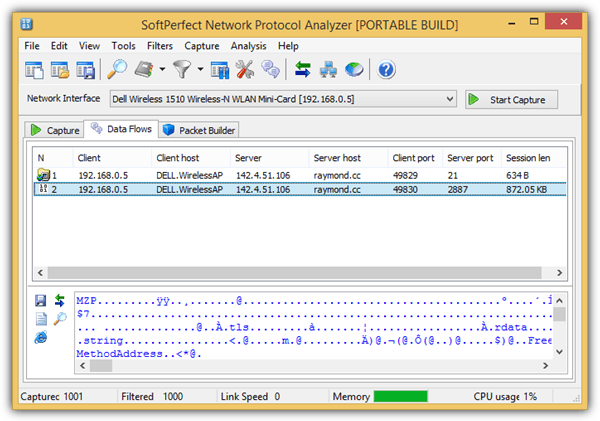
Take note of the server port and the session length. If you see a port 21 followed by a larger size of the session length, it is probably a file being transferred. Select the data flow and click on the save icon located at the bottom left, followed by selecting “Save as Raw Data”. You can then use any of the tools mentioned on this article to identify the file type. Alternatively if the file is relatively small, you can upload it to an online TrID File Identifier to identify the format of the file.
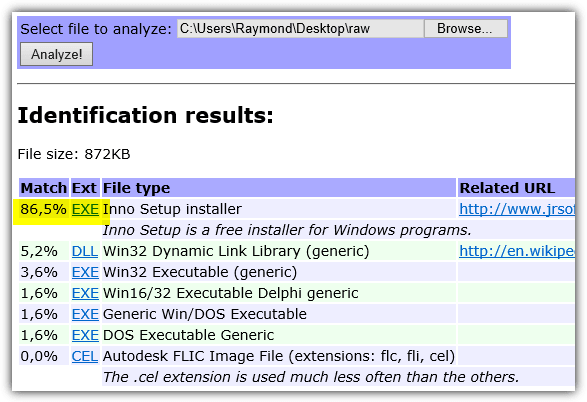
An advanced user can instantly tell that the first few byte showing “MZA” is an executable file.
Download SoftPerfect Network Protocol Analyzer
3. NetworkMiner
NetworkMiner is actually a very powerful network forensic analysis tool and more user friendly if compared to WireShark. The file reconstruction works fine on an Ethernet adapter but the wireless capture requires an AirPcap adapter to work best while the internal wireless adapters will most likely fail to reassemble any file from a captured packet. However other features such as extracting login credentials will still work.
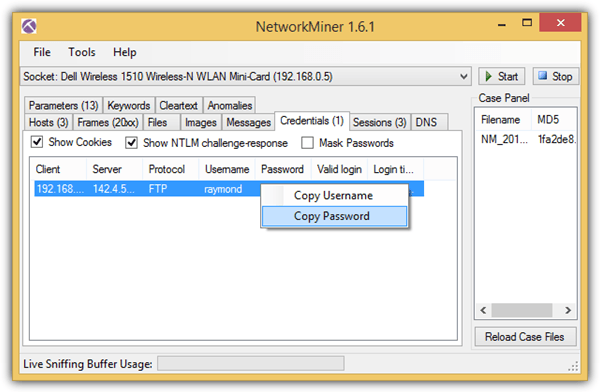
Another advantage in NetworkMiner is the ability to parse PCAP files exported from other packet capturing software such as WireShark and tcpdump.
4. Wireshark
Although Wireshark is mostly used by professionals to capture and analyze packets because it is not very user friendly, we find that it is actually quite easy to find FTP transmitted data by using the search function, follow the TCP stream and finally save the entire conversation as a raw file.
At the Filter bar, type ftp-data into the box and press Enter. Click on Analyze at the menubar and select “Follow TCP Stream”.
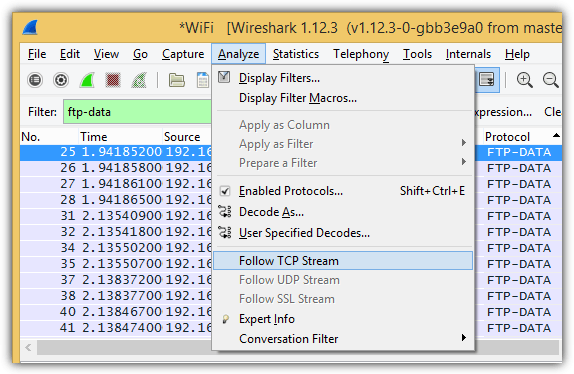
Take note of the first few bytes in the stream content which will give you an idea of the file extension. The below example shows PK which is a ZIP file format. In fact, the file header also shows the filename of the zip file which is arpfreezeNG.
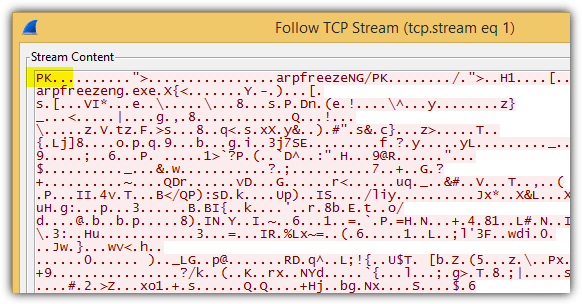
To reconstruct the file, simply select Raw and click the Save As button. Since this is a zip file, you should save it with a .ZIP extension and preferably as arpfreezeNG.zip if you’d like to preserve the original filename.
5. SmartSniff
SmartSniff is a free packet sniffer created by Nirsoft and a very useful feature found on this tool is the ability to capture using raw sockets and without the third party WinPcap driver. However, the raw sockets method is known not to work on all systems due to the Windows API. If you’ve captured a lot of packets, it may not be easy to look for the packet data containing the transferred files.
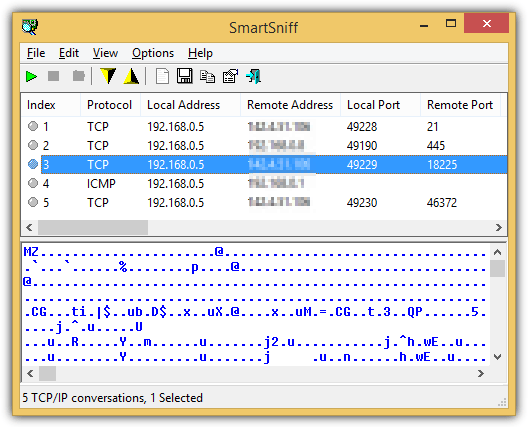
As you can see from the screenshot above, the first few bytes shown at the lower pane does give you a hint that the raw data is an executable file. Press Ctrl+E to export the TCP/IP streams and make sure to save it as “Raw Data Files – Local (*.dat)” type. Rename the .dat extension to .exe and you get the reconstructed file.


nice post budy…
This is very interesting and useful information.
Nice digging!
thanks so much for this … raymond..
Good find. This product needs some tools for configuration, i.e. where to store the captured files, or filters on what to capture or what to see, etc.
Thanks for this article Ray.