Remotely Crash Windows 7, Vista, XP and Server 2008 with Blue Screen of Death

A Windows operating system contains roughly 40 to 50 million lines of code and there is definitely programming errors that can cause problems in Windows which is up to security experts or hackers to find an exploitable backdoor. This is why it is very important for a computer running Windows operating system especially the ones that are connected to the Internet to be always up to date with the current patches or hotfixes to ensure that it is stable and reliable.
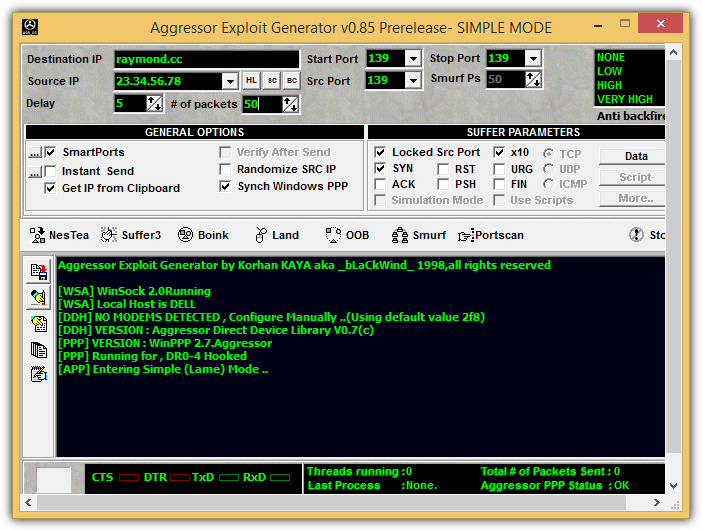
It is comforting to know that each newer version of Windows is less vulnerable to remote attacks that can crash the computer with blue screen of death. Back in Windows 95, there were many different types of Denial of Service attacks that can cause the system to lockup. Furthermore, not many users were aware of Windows Update to automatically check and install security updates at that time and most of these attack tools are easy enough for beginners to use by just entering the victim’s IP address. Even the most advanced Windows attack tool back then called Aggressor Exploit Generator has a simple mode that can launch NesTea, Suffer3, Boink, Land, OOB and Smurf attack from Windows 95 with a mouse click.
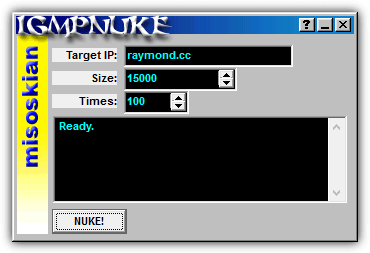
All DoS tools that can crash Windows 95 was fixed in Windows 98 but then it was vulnerable to large IGMP packets. An IGMP Nuker created by Misoskian is available publicly for anyone to use it to crash Windows 98 system by simply entering the remote computer’s IP address.
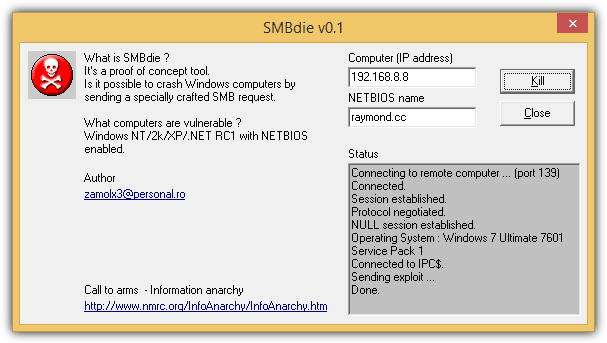
Windows XP came later but wasn’t spared from nuke attacks as well. Zamolx3 created a proof of concept tool to easily crash Windows XP with blue screen of death by sending a specially crafted SMB request to a XP computer by just specifying the IP address and computer name. Although SMBDie requires an additional information which is the NETBIOS name, getting it is easy enough by pinging the IP address with -a switch. Anyway, computers running Windows XP without any service pack installed is vulnerable to this attack.
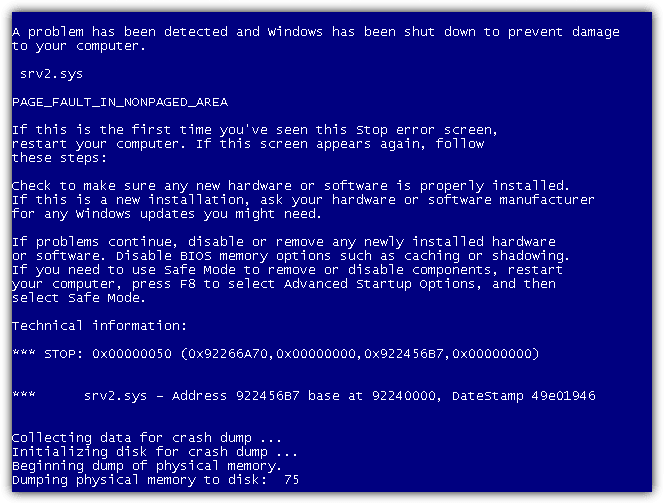
Most people would agree that Windows Vista isn’t very stable although the graphical user interface looks nice. It is safe from the SMBDie attack, but unfortunately the newer SMB2.0 suffers from another vulnerability that can cause a BSOD. If the victim’s computer running Windows Vista does not have the patch installed and the Windows Firewall is disabled, a blue screen with the error PAGE_FAULT_IN_NONPAGED_AREA caused by srv2.sys will be presented.
The original attack script is written in Python. Running the script in Windows is as easy as installing ActivePython, edit the script to replace the IP_ADDR with the victim’s IP address, save the changes and run it. There are quite a few Windows binary version that is easy to use but one that is still available is SMB2Nuke by www.illmob.org. Similarly to the good old WinNuke tool, simply enter the victim’s IP address and click a button to launch the attack.
A newly installed Windows Vista that hasn’t been updated yet is definitely vulnerable to SMB 2.0 nuke but then the Windows Firewall that is turned on by default is able to protect against the attack. You can download the official update MS09-050 from Microsoft Security TechCenter. Windows 7 is mostly safe from SMB2.0 attack because only the Release Candidate (RC) version is affected.
While security vulnerabilities exist in every version of Windows, the operating system is quite safe against these attacks as long as there are no proof of concept being published publicly where anyone can abuse it. There was a case in 2012 where security researcher Luigi Auriemma found a vulnerability in Remote Desktop. Someone else got hold of the code and released their Proof of Concept tool in a Python script that can crash a Windows computer with Remote Desktop enable with blue screen of death.
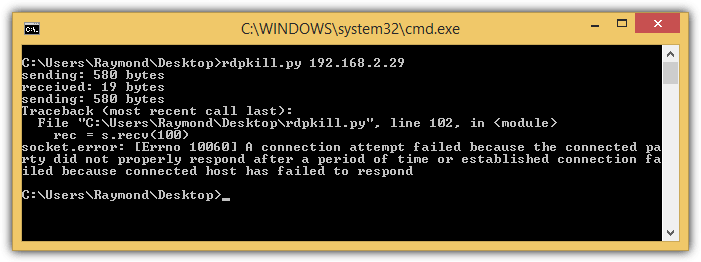
illmob.org made the attack much more easier to run through a Windows executable program. Simply download, run, enter the IP address of the computer with Remote Desktop enabled and click the “Nuke it!” button. The victim’s computer will instantly get a blue screen showing an error with the affected file termdd.sys. The termdd.sys file is a remote desktop server driver so it gives you a hint that the blue screen is caused by Remote Desktop.
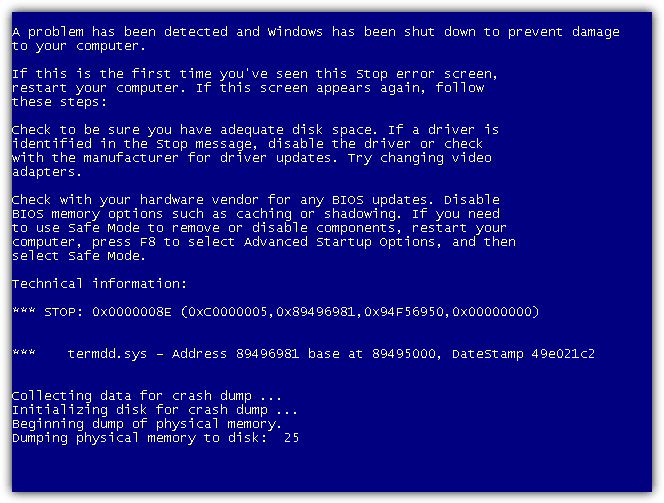
Windows XP, Vista and 7 are vulnerable to MS12-020 attack. If your computer is not fully up to date for some reasons, you can manually download and install the MS12-020 patch from the official Microsoft’s website.
Final Notes: As you can see, keeping your Windows operating system up to date is vital in preventing against attack from known vulnerabilities. You will also need to make sure that the third party software are always up to date as well, and also having a good antivirus software protecting your computer against malicious software is equally important.



User forum
15 messages