5 Invisible Watermark Software to Stop Image Theft For Good

My search for the best invisible watermark tool started when a friend of mine, a talented designer, once discovered his work on a big website, no credit, no permission.
Watermarks were cropped, and right-click blockers were useless against browser tools like Firebug that can monitor HTTPS and reveal the image’s URL.
That’s when I realized invisible watermarks were the answer. They’re discreet, provide proof of ownership, and make takedowns easier. Here are a few reliable tools I found
Invisible Watermark Software
Below, I explain what the best watermarking tools we found do, showcase their features, and explain how you can use them for content protection.
1. Pixsy – Comprehensive image monitoring and anti-piracy protection
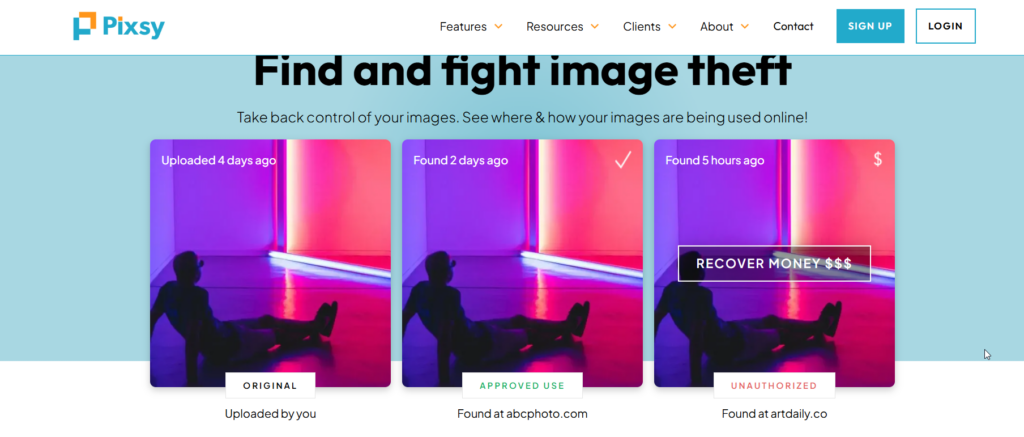
Pixsy is a leading platform for digital rights management, offering robust image protection through forensic watermarking.
It allows photographers and creators to protect their work and track its usage across the internet, making it easier to address piracy.
- Image Monitoring: Tracks how your images are being used across thousands of websites.
- Anti-Piracy Measures: Helps detect unauthorized use and offers tools for easy takedown requests.
- Supported Formats: Compatible with JPEG, PNG, and more, ensuring versatility.
With Pixsy, you get more than just watermarking. The platform also provides the ability to file legal claims against unauthorized use, making it a great choice for comprehensive digital rights management.
2. Digimarc
Digimarc’s digital watermarking technology provides secure, invisible identifiers for various media types, helping businesses protect their assets.
It integrates seamlessly with widely used software and supports multiple file formats, ensuring versatility across images, audio, and video.
- Formats Supported: JPEG, PNG, TIFF, WAV, MP3, MP4
- Seamless Integration: Works with tools like Adobe Photoshop and Illustrator
- Versatile Use: Applied to both raster and vector images, audio files, and videos
It integrates smoothly into existing workflows, enhancing security without disrupting the creative process.
As for the cost, Digimarc offers customized pricing based on usage and business needs, with flexible plans to suit different scales.
3. Imatag
Imatag offers an invisible digital watermarking solution designed to protect your visual content and ensure proof of ownership.
It’s an ideal choice for photographers, artists, and businesses that need secure and tamper-proof content protection without altering the image’s appearance.
- Invisible Watermarks: Adds pixel-level embedding watermarks without disrupting the design.
- Forensic Watermarking: Perfect for tracking and detecting unauthorized usage across the web.
- Easy to Use: Integrates with existing workflows to streamline content protection.
Imatag helps you stay on top of your image monitoring efforts by providing detailed reports on where and how your images are being used. Whether you’re looking to prevent piracy or enforce copyright protection, this invisible watermark software is a powerful, non-intrusive solution.
4. Icemark
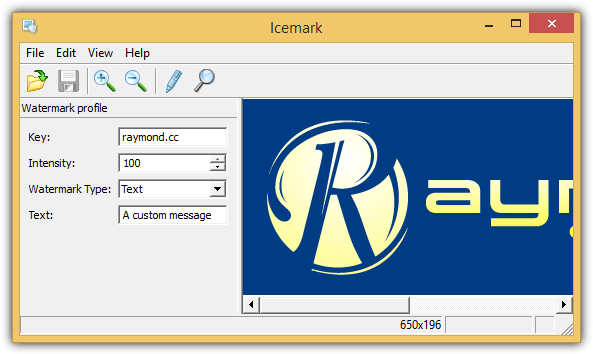
Icemark is a shareware product that can embed an invisible watermark into digital images. It’s a paid product, costing $49.95 for a single license.
The tool signs the images with a private key that is known only to you. It offers 3 types of watermarks:
- identification: just watermarks the image as yours
- image ID: also lets you add 3 indicators, such as “Restricted Use”, “Do Not Copy” and “Adult Content”.
- text: works similarly to image ID, but lets you enter your own text.
Batch processing is available in File menu where you can automatically process multiple embeddings or detections.
Images that are watermarked with Icemark are resistant to common image editing operations such as compression, distortions, and cropping.
To detect the invisible watermark signed by Icemark, load the image into the program, click the magnifying glass icon and it will tell you if the watermark is detected or not.
Make sure the correct private key is entered before detecting the watermark.
5. OpenStego
OpenStego is an open-source application that can watermark images using an invisible signature. Using it is very straightforward:
- The first step is to create a signature file based on the passphrase.
- Then use the signature file to watermark the images.
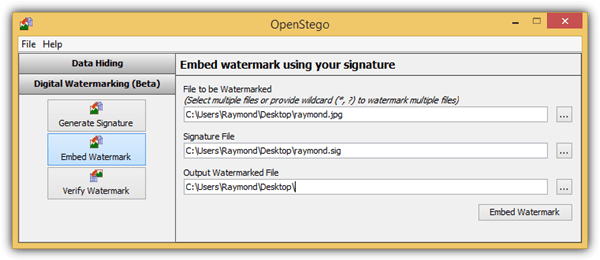
OpenStego runs on Java, and the digital watermarking feature is still in beta. The tool is compatible with Windows and Linux, and the latest version, OpenStego 0.8.6, was released on January 30, 2023.
As an open-source project, OpenStego allows users to access its source code for transparency and customization. It is widely used by the general public for digital watermarking and covert data transmission.
With so many crafty and talented content thieves out there, it’s become clear that protecting digital work is more important than ever.
Invisible watermarks have become a game-changer for me, providing a discreet but powerful way to safeguard images and ensure proof of ownership, all without altering the design.
If you’re looking to further improve your image editing workflow, consider checking out how to open PSD extension files without Adobe Photoshop or compare the differences between two identical-looking images. Additionally, if you’re in the business of printing, finding the best sublimation software could be a great step forward in securing your designs.



User forum
12 messages