3 Methods to Spoof Fake File Extensions in Windows

A filename extension is very important in the Windows operating system and it appears at the end of the file name. Not only can you instantly tell what type of file format, whether it is an image or an executable application, Windows can also decide what program to launch it with based on what is registered in the default programs list.
Generally you should pay more attention to the executable file format such as .EXE .COM .SCR .BAT .VBS .PIF and .CMD because it can be malware instead of a legitimate program. For example, an ebook that should be in a PDF or EPUB extension shouldn’t be .EXE although it is still possible if it is wrapped with a third party ebook compiler to protect against illegal distribution.
Since Windows users are more careful with executable extension and pay less attention to safer extensions such as image formats, there are a couple of ways to trick the careless user into thinking that an EXE file is a JPG image file instead.
1. Hide Extensions for Known File Types
There is a setting in Folder Options where you can hide the file extension so that only the filename is visible in Explorer while the extension is hidden. The problem with this setting is the default option is set to hide and a less careful user can be tricked when there is a double extension. An example of a double extension is:
notes.txt.exe
The file above is actually an executable file but is shown as notes.txt with the .exe hidden due to the Folder Option setting. The next step to make the file look more convincing is to change the file icon to Notepad icon. As you can see from the example image below, it looks like a normal text file.
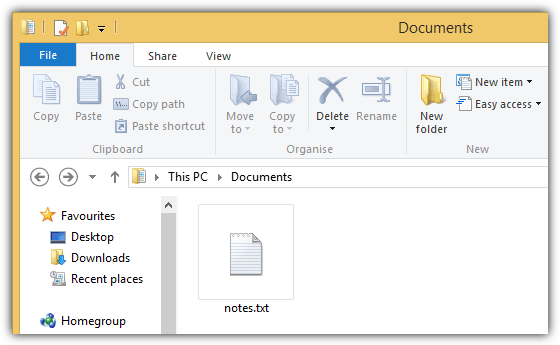
If you change the view type to “Details”, it shows very clearly in Explorer that the so called notes.txt file is actually an application.
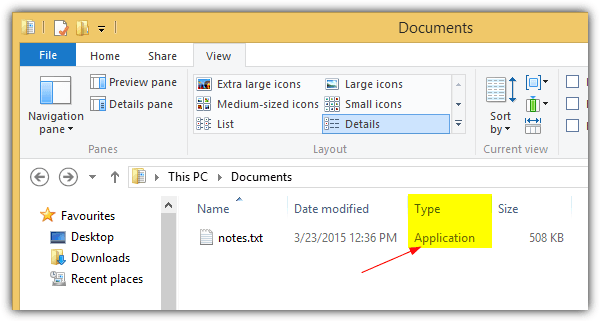
You can confirm this further by right clicking on the file, selecting Properties from the context menu and viewing the “Type of file” which should show Application (.exe).
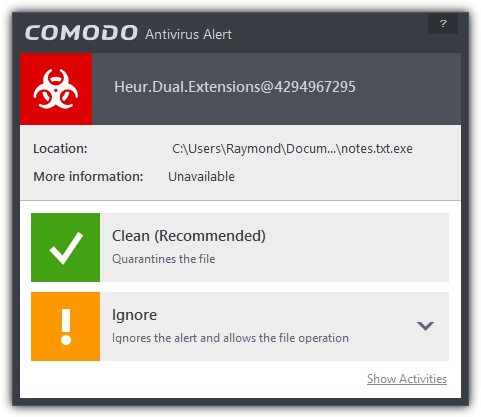
This is a very old trick and a few antivirus applications like COMODO will warn you when it detects a double extension in a filename.
An easy solution to prevent you from falling into the double extension trick is to disable the “Hide extensions for known file types” option from Control Panel > Folder Options > View tab.
2. Right to Left Override
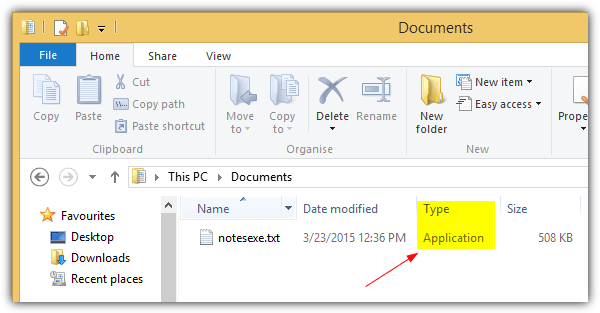
This trick uses Right to Left unicode to reverse the last six characters so that the extension is spoofed. For example, a notes.exe file can be renamed to notesexe.txt. Although the file extension clearly shows as .txt in Explorer, the Windows operating system still recognizes the file as an application.
Since the Right to Left override character cannot be typed from the keyboard and is only shown in the Character Map program found in Windows, one can simply download a free third party program called BabelMap to generate the RTLO character for copying to clipboard and paste it when renaming a file.
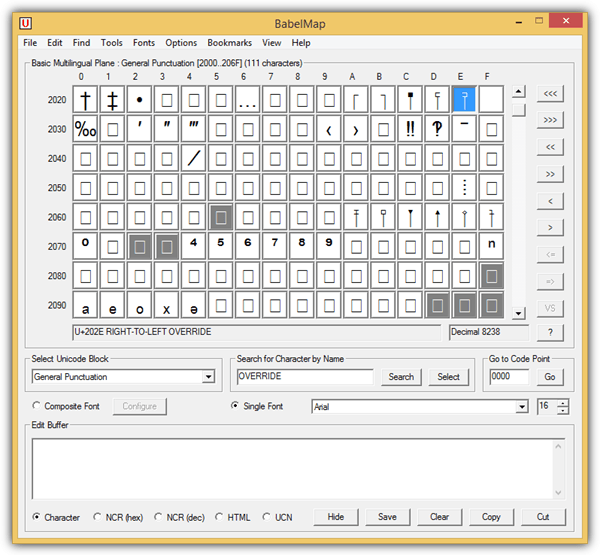
Fortunately most major web browsers have stepped up to blacklist the right to left override character so that the correct file extensions are shown correctly when a user attempts to download the file with a spoofed extension using the RTLO trick. Other than that, using the “Details” view in Explorer can greatly help you to determine the correct file type.
3. Software Exploits
An older version of WinRAR 4.20 is vulnerable to file name and extension spoofing. This means you can modify the ZIP file created by WinRAR 4.20 using a hex editor to show a different filename and extension in the GUI but another different extension when it is run directly from the program. An example is a notes.exe file compressed into a notes.zip using WinRAR 4.20. Then using a hex editor, go to the end of the file and modify the notes.exe to notes.txt.
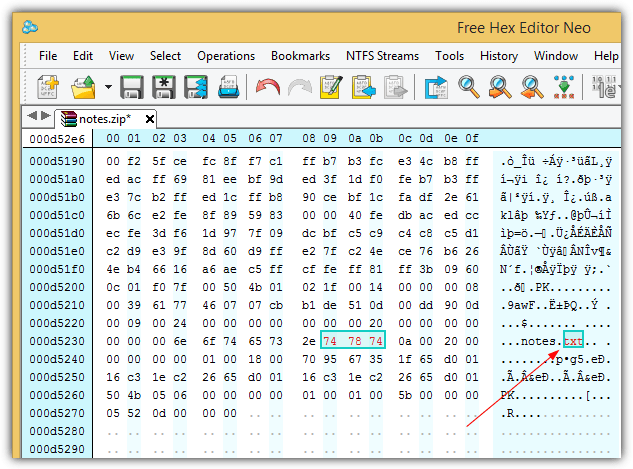
Opening the notes.zip file in WinRAR 4.20 will now show the archived file as the spoofed notes.txt instead of notes.exe.
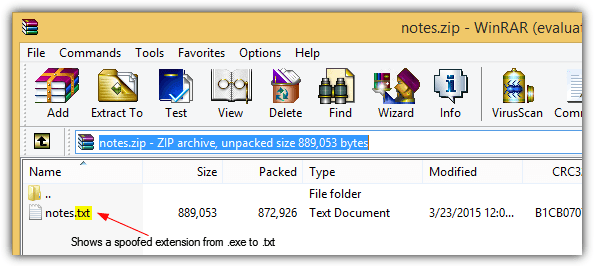
Double clicking on the spoof file from WinRAR GUI will run the file as application. However people who extract the file will be safe from this spoofing exploit as they will see that it is an executable (.exe) file being extracted, not a text (.txt) file.
WinRAR 5 and above has been patched from this exploit. Hence it is always advisable to keep your software up to date even if it is not an internet related application.



User forum
13 messages