Best Keystroke Encryption Software [2023 List]

Secure your devices with award-winning cybersecurity technology.

Browse the web securely for up to 3 devices across Windows, Mac, iOS or Android systems.

Best security tool for intense browsing activity.

Keep secure with groundbreaking AI detection and prevention technology.

Prevent data breaches and malware infections with user-friendly controls.
Performing Some Basic Tests
In this series of basic tests, we will attempt to tamper with the application by terminating its process to see if the protection is still active, and uninstall silently without the user noticing it. The UpperFilter registry key for the keyboard will also be deleted to determine if they are able to detect and recover automatically. Finally, the memory and CPU usage are also measured to see how heavy they are on system resources.
1. GuardedID Premium 3.01.1060
Process Termination: FAILED
Silent Uninstall: YES. Can be silently uninstalled using this command line “msiexec.exe /x ({ID} /q”. The ID can be found in the registry HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall.
Delete UpperFilters: FAILED. Keyboard stops working.
Memory Usage: Starts at 1.8MB and increases a bit on every keystroke
CPU Usage: NONE
2. Zemana AntiLogger Free 1.5.2.652
Process Termination: PASS. Protection is still active when the process is terminated.
Silent Uninstall: YES. Installer uses Inno Setup and can be silently uninstalled with the command line “unins000.exe /VERYSILENT”
Delete UpperFilters: FAILED. Keyboard stops working. Program detects the problem when Windows is booted up and offers to automatically repair by rebooting the computer. Failed to auto repair even when logged in as an administrator with UAC turned off.
Memory Usage: 14MB
CPU Usage: NONE
3. KeyScrambler Premium 2.9.3.0
Process Termination: FAILED
Silent Uninstall: YES. KeyScrambler installer uses Nullsoft Scriptable Install System (NSIS) and supports the silent uninstall switch /S.
Delete UpperFilters: Keyboard stops working.
Memory Usage: 1.5MB
CPU Usage: NONE
4. NextGen AntiKeylogger 3.3.0.1
Process Termination: FAILED. Has an option to keep protection active when process is terminated but didn’t work for us.
Silent Uninstall: YES with the command line parameter /VERYSILENT (uses Inno Setup) but not fully automated because it prompts a survey window that cannot be suppressed. Do take note that the uninstaller does not prompt for password when the program is protected with a password.
Delete UpperFilters: Keyboard stops working and notifies about a failure in connecting to driver with an advice to restart your computer or reinstall.
Memory Usage: 3.7MB
CPU Usage: NONE
Running a Keylogger Test
We tested the keystroke encryption software with a total of 13 well known keyloggers that are widely being used today. 5 of them are Remote Administration Trojans (RAT) with keylogging functionality and the remaining 8 are pure keylogging programs where 3 of them; Elite Keylogger, Invisible Keylogger Stealth & Keylogger Pro 2012 use low level keyboard hooking. The tests were ran on a clean Windows 7 Ultimate 32-bit by installing or activating the keylogger and typing a few sentences. The log files from the keyloggers were then reviewed to see if it managed to capture the real text or not.
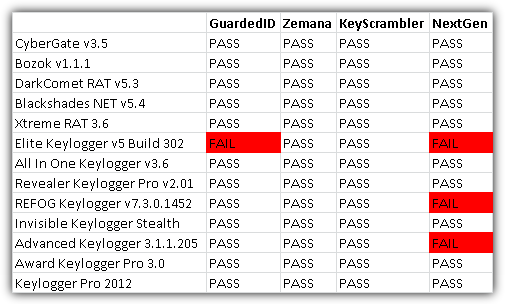
As you can see from the results above, only Zemana AntiLogger Free and KeyScrambler Premium passed all 13 tests by preventing the keyloggers to record the text that was typed from the keyboard.
The Verdict
Without a doubt that the new comer Zemana AntiLogger Free emerges as the best keystroke encryption today followed by KeyScrambler. The “free” price tag on Zemana easily beats the rest because it protects all applications unlike the free version of KeyScrambler and NextGen AntiKeylogger that only protects the well known major web browsers. Would be nice if Zemana has a feature that allows the user to manually exclude an application since it blocks all applications when the protection is active.
Additional Note: Although keystroke encryption provides really good protection against keyloggers, but they don’t protect you against form grabbing which is a pretty old method found in advanced malwares to grab the POST data from your web browser. They can however be prevented by some antivirus that can detect code injection and API hijacking on web browsers.

Theses scramblers and encryption software sound good until you install them, Then you find out the logger disables the software or browser before you get past typing in the first keystroke of a password.
1. This review is missing SpyShelter which is the only application that works with East Asian languages which is a huge thing for people like me.
2. Zemana AntiLogger Free has been discontinued for a long time, used it previously.
Note that SpyShelter Free version has been discontinued and only the paid version is available.
Well what I thought looking at this blog for a while now – it’s hard to keep it running fully supported – right? I tried the same about other subjects and met early the same matter.
Sad to tell now that Zemana has officially stopped to offer a free version…”politely” announcing that the free version will not be continued / supported any longer – haha.
Just waiting to blackmail enough users hung up on the free version now – as it’s done almost everywhere.
Well, that’s all for now…
E. A.
zemana seems to be making my chrome not able to use keyboard
Actually nowadays SpyShelter’s keystroke encryption is the best. It has the lowest input lags and is the only application that encrypts keystrokes of all aplications, unlike keyscrambler where you have to pay more to protect specific apps!!
Hi Raymond, I am interested in a keylogger encryption tool for a very large group into the thousands. At this stage are you still recommending Zemana over all others? I noticed they are located out of the country, I’ve written to them to see if they have USA representation. I’m going to due diligence. Your post looks like it’s over a year old now. Any advice on choosing the best provider in this space? Thanks!
Hello Raymound i wanna ask you if i can use GuardedID and Zemana at same time with Avast? or will have a trouble in my pc ? also i want ask you if GuardedID and Zemana will slow my pc cause at this moment i have only 1.5 gb ram, thank you!
Hi Raymond !
I tried Zemana and saw that it does not prevent windows snipping tool ! I think that could be used to bypass screen capture. I don’t know computer science, but I don know a little bit about computers. I guess that it might be possible for malware to make snipper take the screenshots secretly, store them temporarily and upload them to a server. Is that possible ? That would be a big fail if true :)
Thank you for the info Raymond. You mentioned “Zemana blocks all applications when the protection is active.” Can you elaborate a bit more on that? If i use Zemana, should i only activate it at certain times? Can you activate it for 24/7/365 usage, or will that slow my PC down? Or is it best that we activate it only when we use our credit cards online? I would prefer to use it 24/7/365 to also prevent my communication to friends from being stolen. Thank you very much
Unlike KeyScrambler Premium that only protects a list of supported applications, Zemana works on all applications. Unless there is a conflict, it is best to keep Zemana active at all times as it doesn’t slow down your computer at all.
Zemana is no longer free, demo and SAAS crap now…..annual fee.
Would luv to see the results for Spyshelter (Latest VErsion) that now has keyboard encryption
Thanks for this info. I would really install Zemana Antilogger Free for my laptop. This is really great for a free program.
So what actually was recorded with Zemana and Keyscrambler. It’d be interesting to see, unless it’s just blank and the key logger complete fails to record anything with those programs.
Zemana outputs blank while KeyScrambler random characters. Please check the part where it says “Encryption Method”
thanks for your articles.i usually check ur site for new articles.
Hi Raymond
I want to ask can I use together Zemana AntiLogger Free and KeyScrambler free?
Zemana for my folders and KeyScrambler for Internet!!
Hi John,
Zemana AntiLogger Free and KeyScrambler free does the same thing, so you should not be using them simultaneously. Do note that the free version of KeyScrambler only protects your web browser while Zemana AntiLogger Free protects all programs.
A very important point that was not included and I was stung by. I main host machine contains all my sensitive data…I connect to this machine using remote connection when away from home (ie logmei.com / Teamviewer etc). Keyscrambler will NOT work over remote connections…the vendor has confirmed this too me after I purchased the full product. So…if all the other products are the same…there is your major security flaw. If you host has a keylogger…and you connect to the host remotely…your keystroke software will NOT encrypt typed keys from remote connection. Major Fail.
Thanks for pointing this out Sandu. I too confirm your findings after testing it.
Sending keystrokes from the real keyboard and remote connections is quite different.
I believe the remote connection is similar to using the on-screen keyboard utility where the keystrokes doesn’t get encrypted.
Silly question: Do these programs protect portable programs against Keyloggers?
I use Firefox Portable as my main browser these days (and occasionally use LibreOffice Portable) and was wondering would portable programs be protected if I installed one of these programs on my computer?
Yes, these programs protect portable programs against keyloggers as long as they are in the list of supported applications.
Merci Raymond, j utilise keyskrambler depuis plus de deux ans, il est super ! passe un tit coucou à la p’tite ! j ‘espère qu elle va bien ! @ très bientôt.
SpyShelter Personal (Free) is the best.
What about Comodo Int. Security, does it protect fom keylogger?
This is why I read your blog. Excellent work.
Thanks Raymond. Used Zemana for a couple years now but didn’t realize I failed to install it on this very machine after a rebuild!
Please advise:
“Delete UpperFilters: FAILED. Keyboard stops working. Program detects the problem when Windows is booted up and offers to automatically repair by rebooting the computer. Failed to auto repair even when logged in as an administrator with UAC turned off.”
— Does this mean that the system booted suessfully and you only had to manually reinstall Zemana or that there was a system boot failure that required manual removal of the UpperFilters to fix?
— What recommendation(s) do you make to protect against the more insidious “form grabbers”? I suppose password managers (LastPass, RoboForm), etc.) offer some protection. Since you have to enter data at least once before those apps canbe used, are they enough/any protection?
Thanks and regards. Kinda missed you. :)
Hi JMJ. After manually deleting the UpperFilters for the keyboard as a test, Windows still booted up fine but the keyboard stops working. A simple way to fix it is to reinstall the application which is possible using your mouse. This simple test is to determine whether the application can detect the problem and attempt to auto fix it.
Form grabbers can be prevent by some antivirus such as Emsisoft that is capable of detecting code injection and API hijacking on web browsers. Password managers such as LastPass and RoboForm does not protect you against such attack.
I use KeyScrambler Premium very happy with it I have also used Zemana in the past and also like it Your post was helpful to me Thanks
Zemana Antilogger is the best !!!
Hi,
Really nice to se you back!!!
Keep doing good job.
Hello Raymond . . . Glad to see that you are back!
I have the Premium version of Keyscrambler and so far am pretty happy with it – – In fact, I LOVE it!
The Man behind Keyscrambler, Mr. Chen, does attend to the needs of his subscribers and is open to suggestions to improve said software (in fact, he immediately corrected a typo I once discovered on his nice-looking website).
He is a good customer care person as demonstrated by his prompt response to inquiries (as he has done in the past regarding my case).
I recommend Keyscrambler to friends and colleagues and they too are impressed about how it makes them feel safer while traveling on the Internet.
I am certain that he has seen today’s review and will do his best to make this an even Better product!
Thank You for Listening (as always),
TheRube
Hi TheRube,
Yes, the guy behind KeyScrambler is a very nice guy. Talked to him a few times via email and he’s always very polite. I’ve in fact forwarded this URL to him to consider adding the extra protection to the upcoming 3.0.
Hi Ray,
very nice tests. how about spyshelter firewall beta 2.0. it now has a keystroke encryption. many would like to see the test results on win 7 x64
Thanks
Hi John,
Thanks for informing me about spyshelter firewall beta 2.0 that comes with keystroke encryption. We’ll add it to this post once the program is out of beta. We prefer not to encourage “beta” versions especially security software.
Thanks Raymond. I was just discussing keyloggers yesterday with a co-worker. I will follow your suggestion and install the recommended software tomorrow. I’ve also forwarded this to my professional circle.
Thank you Josh. Hope it helps!
Hey name sake,
Thanks for sharing this crucial matter witrh us. Jeep it up!
Hugs
Thanks Raymond again.
Keep making these excellent reviews. Cant wait to test Zemana Antilogger :)
Zemana Antilogger is the best ;)
I use Zemana AntiLogger (paid)…………
Currently the paid version of Zemana AntiLogger doesn’t have keystroke encryption built-in to the program but it will in future.
I know it Ray,thank you very much!
Thanks for the heads up Raymond.
How are you and your family :) ??
We’re fine, thanks for asking :)