Best Keystroke Encryption Software [2023 List]

Performing Some Basic Tests
In this series of basic tests, we will attempt to tamper with the application by terminating its process to see if the protection is still active, and uninstall silently without the user noticing it. The UpperFilter registry key for the keyboard will also be deleted to determine if they are able to detect and recover automatically. Finally, the memory and CPU usage are also measured to see how heavy they are on system resources.
1. GuardedID Premium 3.01.1060
Process Termination: FAILED
Silent Uninstall: YES. Can be silently uninstalled using this command line “msiexec.exe /x ({ID} /q”. The ID can be found in the registry HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall.
Delete UpperFilters: FAILED. Keyboard stops working.
Memory Usage: Starts at 1.8MB and increases a bit on every keystroke
CPU Usage: NONE
2. Zemana AntiLogger Free 1.5.2.652
Process Termination: PASS. Protection is still active when the process is terminated.
Silent Uninstall: YES. Installer uses Inno Setup and can be silently uninstalled with the command line “unins000.exe /VERYSILENT”
Delete UpperFilters: FAILED. Keyboard stops working. Program detects the problem when Windows is booted up and offers to automatically repair by rebooting the computer. Failed to auto repair even when logged in as an administrator with UAC turned off.
Memory Usage: 14MB
CPU Usage: NONE
3. KeyScrambler Premium 2.9.3.0
Process Termination: FAILED
Silent Uninstall: YES. KeyScrambler installer uses Nullsoft Scriptable Install System (NSIS) and supports the silent uninstall switch /S.
Delete UpperFilters: Keyboard stops working.
Memory Usage: 1.5MB
CPU Usage: NONE
4. NextGen AntiKeylogger 3.3.0.1
Process Termination: FAILED. Has an option to keep protection active when process is terminated but didn’t work for us.
Silent Uninstall: YES with the command line parameter /VERYSILENT (uses Inno Setup) but not fully automated because it prompts a survey window that cannot be suppressed. Do take note that the uninstaller does not prompt for password when the program is protected with a password.
Delete UpperFilters: Keyboard stops working and notifies about a failure in connecting to driver with an advice to restart your computer or reinstall.
Memory Usage: 3.7MB
CPU Usage: NONE
Running a Keylogger Test
We tested the keystroke encryption software with a total of 13 well known keyloggers that are widely being used today. 5 of them are Remote Administration Trojans (RAT) with keylogging functionality and the remaining 8 are pure keylogging programs where 3 of them; Elite Keylogger, Invisible Keylogger Stealth & Keylogger Pro 2012 use low level keyboard hooking. The tests were ran on a clean Windows 7 Ultimate 32-bit by installing or activating the keylogger and typing a few sentences. The log files from the keyloggers were then reviewed to see if it managed to capture the real text or not.
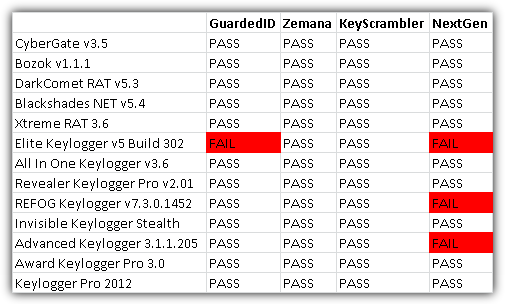
As you can see from the results above, only Zemana AntiLogger Free and KeyScrambler Premium passed all 13 tests by preventing the keyloggers to record the text that was typed from the keyboard.
The Verdict
Without a doubt that the new comer Zemana AntiLogger Free emerges as the best keystroke encryption today followed by KeyScrambler. The “free” price tag on Zemana easily beats the rest because it protects all applications unlike the free version of KeyScrambler and NextGen AntiKeylogger that only protects the well known major web browsers. Would be nice if Zemana has a feature that allows the user to manually exclude an application since it blocks all applications when the protection is active.
Additional Note: Although keystroke encryption provides really good protection against keyloggers, but they don’t protect you against form grabbing which is a pretty old method found in advanced malwares to grab the POST data from your web browser. They can however be prevented by some antivirus that can detect code injection and API hijacking on web browsers.



User forum
46 messages