8 Websites to Search for Ransomware Decryptor Tools

Ransomware is a type of malicious software that has been gaining popularity lately and it is actually similar to kidnapping if put into real life cases. When a ransom is paid, the victim may (or may not) be released. Hackers have extended this idea to computers, basically creating malware that takes control of your computer by restricting you from using it, or it can also restrict you from accessing your important files such as documents and photos.
Locking up computers and asking for ransom is ineffective because it is easy to fix. Anyone who knows how to use a rescue disk to boot up the computer can easily remove the malicious file from Windows startup. It didn’t take long for the hackers to realize this and they’re now using a more effective approach which is taking your important file such as photos and documents hostage by encrypting them with really strong encryption that is virtually unbreakable.

Breaking an encryption algorithm is not something that a computer technician or engineer is capable of, so the probability of getting back your files by sending it to a computer shop is close to zero. If you do not have a backup of the files encrypted by the ransomware and the shadow volume copies have been deleted, here we have a few resources to search for the possibility of decrypting the encrypted locked files without paying the ransom.
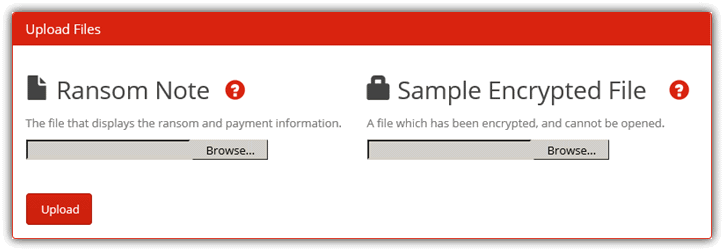
Before you start scouting for ransomware decryption tools, you’ll first need to identify the name of the ransomware that has encrypted your files. Most of the time the file extension of the encrypted file gives a hint of the type of ransomware that encrypted your files. The easiest way is to visit a website called ID Ransomware where it is currently able to identify 162 different types of ransomware. All it needs is the ransom note or a sample of the encrypted file.
Once you know the name of the ransomware that encrypted your files, you can search if there is a decryption tool available to decrypt the files encrypted by the ransomware. Most of these decryptor tools are created and offered for free by antivirus companies.
1. Trend Micro
Trend Micro Ransomware File Decryptor tool is able to decrypt files encrypted by CryptXXX V1/V2/V3/V4/V5, TeslaCrypt V1/V2/V3/V4, SNSLocker, AutoLocky, BadBlock, 777, XORIST, XORBAT, CERBER V1, Stampado, Nemucod and Chimera.
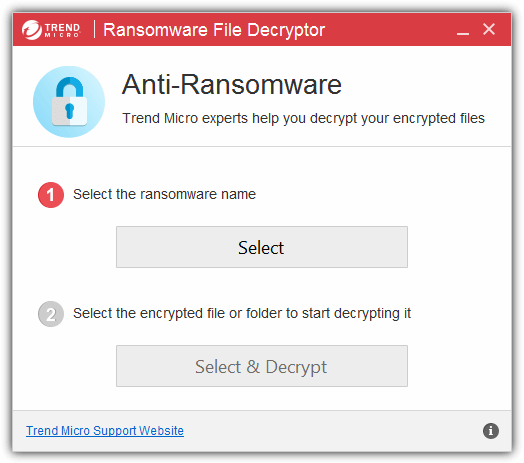
To use this tool, you’ll need to select the ransomware name from the list shown in the program, then choose the files or folders containing the encrypted files to be decrypted. A separate tool called TeslacryptDecryptor can be used if you intend to decrypt files that are encrypted by the older versions of TeslaCrypt V1 and V2. Do take note that there are some limitations of the decryptor tool particularly to files encrypted by the CryptXXX ransomware families such as the decryption process taking up to 2 hours for each files, and some files may not be fully recoverable.
Download RansomwareFileDecryptor and TeslacryptDecryptor
2. Intel Security/McAfee
Intel Security (previously known as McAfee) offers a lot of security related free tools for intrusion detection, scanning, stress testing, spam submission, forensic, assessment, and anti-malware tools. On the same webpage under the Anti-Malware Tools category, you can also find 3 decryption tools for TeslaCrypt, Shade and WildFire ransomware.
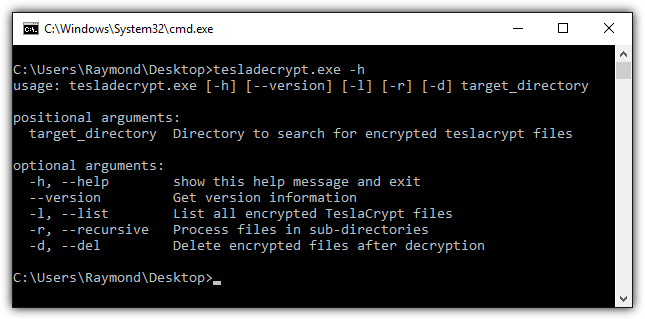
Do take note that Tesladecrypt, Shade Ransomware Decryption Tool and WildFire Ransomware Decryption Tool by Intel Security are command line based which will require manual input of the User ID that is randomly generated by the ransomware. If it is too challenging for novice users to use these command line tools, there are graphical user interface based tools by Kaspersky listed below.
Visit Intel Security Free Tools
3. Kaspersky
There are two webpages where you can find the free ransomware decryptors created by Kaspersky. The first is the Utilities webpage that includes all the tools such as virus removal utilities to disinfect specific malware, decryptor tools, Kaspersky Virus Removal Tool and their Rescue Disk. Another web page called NoRansom is also created by Kaspersky but the webpage only includes decryptors for the newer strains of ransomware.
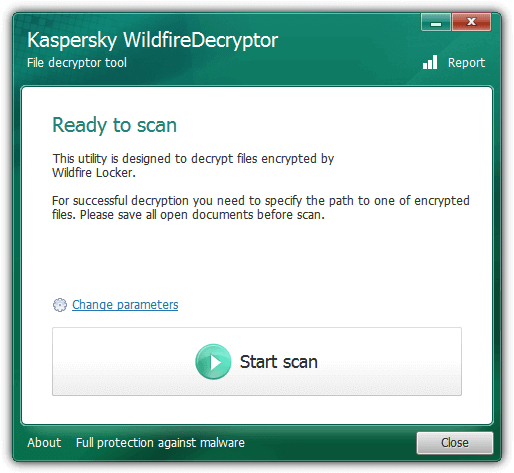
As you can see from the image of a decryptor tool by Kaspersky, it is very easy to use and requires only one click of a mouse button to start the scan and auto decryption. The Change Parameters option allows you to change the objects to scan and also if you’d like to delete the crypted files after decryption.
Currently Kaspersky has released decryptor tools for ransomware such as Wildfire, Shade version 1 and version 2, Xorist, Vandev, Coinvault, Bitcryptor, Rector, Scatter, Scraper, Rakhni and Rannoh.
Visit Kaspersky Utilities Webpage | Visit NoRansom
4. ESET
Although ESET only released 1 decryptor tool, they deserve the credit for the availability to decrypt all files that are encrypted by TeslaCrypt. The story is one of the ESET researchers managed to convince the TeslaCrypt developer to release the master decryption key to public when TeslaCrypt was about to shut down. This is the reason why you’ll find a TeslaCrypt decryptor created by most antivirus companies.
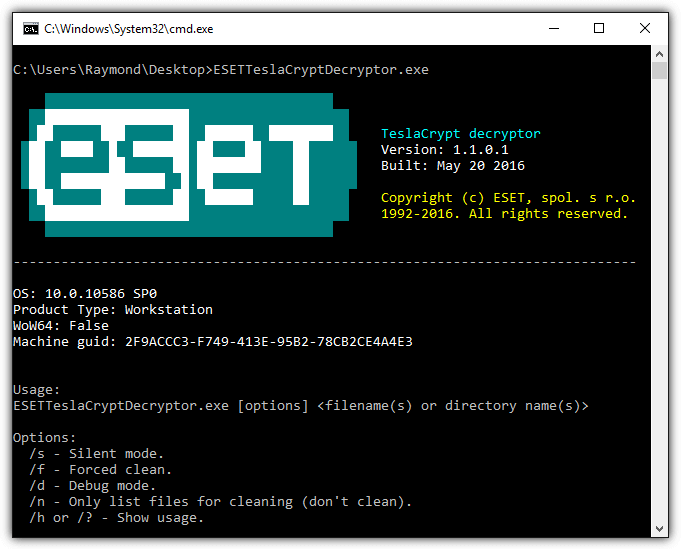
Although ESET TeslaCrypt Decryptor is a command line tool, it is quite simple to use. You’ll only need to include the path or the drive letter in the command line and it will automatically scan the subfolders recursively.
Download ESET TeslaCrypt Decryptor
5. AVG
AVG released decryptor tools for 6 ransomware strains which are Apocalypse, BadBlock, Crypt888, Legion, SZFLocker, and TeslaCrypt. Most of the decryptor tools are very easy to use and already automatically include the root of your drive letters found on your Windows operating system for scanning. Only the decryptors for the new ApocalypseVM and BadBlock require the encrypted file with the original matching file to crack the password.
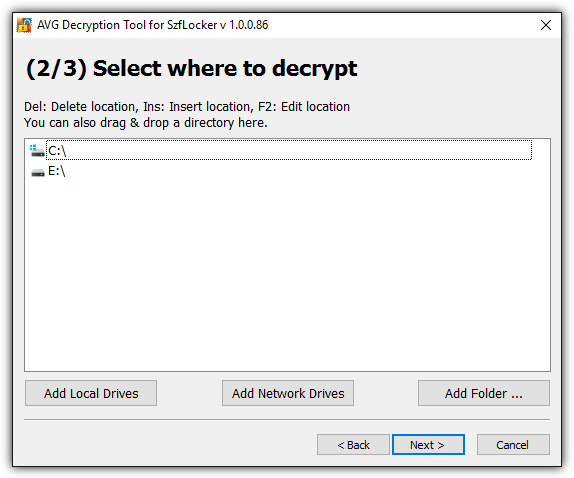
Most of the AVG decryption tools can be run on both 32-bit and 64-bit Windows operating systems except for BadBlock. You’ll need to download the decryptor version that matches your Windows operating system architecture.
6. Emsisoft
Emsisoft has the most decryptor tools to help you recover your files encrypted by ransomware. They currently have 20 decryptor tools that works against Stampado, ApocalypseVM, Apocalypse, BadBlock, Xorist, 777, AutoLocky, Nemocod, DMALocker2, HydraCrypt, DMALocker, CrypBoss, Gomasom, LeChiffre, KeyBTC, Radamant, CryptInfinite, PClock, CryptoDefense, and Harasom.
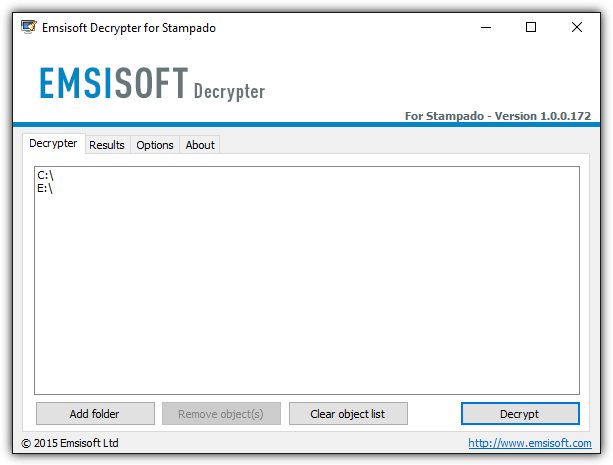
All of the decryptor tools by Emsisoft come with a simple and easy to use graphical user interface. Apart from that, some of the tools are smart enough to automatically look for the decryption key on the infected system.
Download Emsisoft Decrypter Tools
7. Dr.Web
If you’re unable to find a decryptor tool to recover your files for free and you’re willing to fork out money because the files encrypted by the ransomware are very valuable, you can try to submit a request to Dr.Web and see if they are able to decrypt your encrypted files. If the file can be decrypted by Dr.Web, you can purchase the Dr.Web Rescue Pack which includes the decryption service together with a 2 years license of Dr.Web Security Space. The price of the Rescue Pack varies and we’ve read that it can cost up to 150 EURO.
Submitting a request to Dr.Web to decrypt your files is a nobrainer as it is definitely cheaper than paying the ransom. A ransom of 1 Bitcoin may sound very little if you have no idea about the value of Bitcoin but it is around 550 EURO today. Apart from that, paying the ransom doesn’t guarantee that your encrypted files will get decrypted.
Visit Dr.Web Ransomware Decryption Service
8. Bleeping Computer Ransomware Help & Tech Support Forum
When it comes to discussion about ransomware, the Bleeping Computer forum is the most active for this topic and it is also the best place to search for the possibility of decrypting the files encrypted by ransomware. You can also find specific decryptor tools created by their members such as the JigSawDecrypter and NullByteDecrypter by Demonslay335.
Do not lose hope if you’ve discovered from the forum that currently there is no way to decrypt the files encrypted by the ransomware. There is always a possibility of a breakthrough in future that allows everyone to decrypt the encrypted files for free, like what happened when TeslaCrypt’s master decryption key was released to public.
Final Notes: Most of the ransomware would claim to automatically delete the encrypted files if the ransom is not paid within the given time frame. What you can do is make a full backup of your hard drive by creating a disk image so that everything on your computer is being backed up including the ransom note and the encrypted files. This allows the possibility of recovering your files when a decryptor is made available in the near future.



User forum
9 messages