Sandboxie Registry Analyzer Tool: How to Use

Deciding if a file is infected or safe from a VirusTotal scan result can be frustrating when half of the antivirus shows that it is infected while the other half shows that it is clean.
You can try analyzing the half detected file using an online sandbox service such as ThreatExpert but the report only shows the program’s behavior when it’s started and doesn’t tell you what it does when an option is enabled or when a button on the program is clicked.
This is when the sandbox software such as Sandboxie comes to play by allowing you to run any programs on your computer whether they are safe or infected and yet any changes still won’t affect your computer.
Although Sandboxie is mainly used to keep your computer safe by running programs in an isolated space, it can also be used to analyze the program’s behavior.
Here are 2 ways to investigate the changes made to your computer system by programs that are ran inside Sandboxie.
Automatic Analysis using Buster Sandbox Analyzer
Buster Sandbox Analyzer (BSA) is a free tool that can be used to watch the actions of any process that is ran inside Sandboxie. Although BSA is a portable software, it does not work right out of the box and requires a manual one time configuration to load a BSA DLL file by adding 3 lines to the Sandboxie’s INI configuration file.
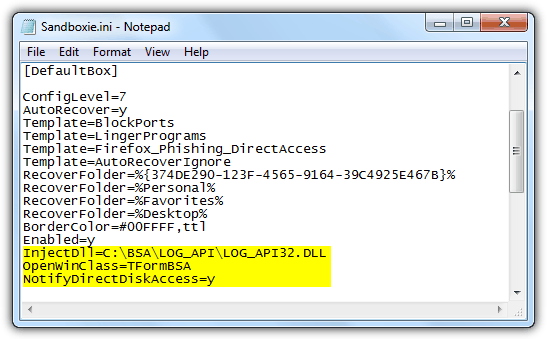
Do take note that if you’re going to follow the exact installation instruction from the official website, you must extract Buster Sandbox Analyzer folder to the root of your C:\ drive. Once that is done, run BSA.EXE executable file from C:\bsa folder and you’ll need to enter the path of the sandbox folder to check which is the location of the Sandboxie’s sandbox folder. To get the location, open the Sandboxie Control by double clicking on the yellow kite tray icon from the notification area, drag any program and drop it to the Sandbox DefaultBox. Now right click on the Sandbox DefaultBox at the Control window and select “Explore Contents”.
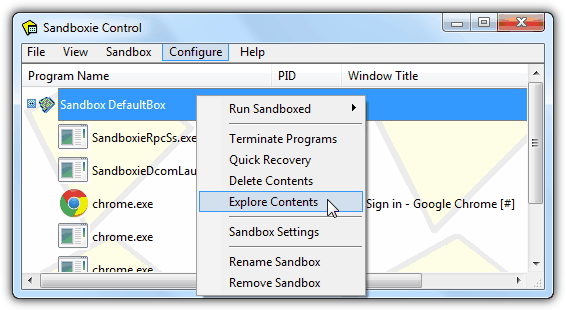
An explorer window will open with the path to the sandbox which you can copy and paste it to “Sandbox folder to check”. Click the Start Analysis button on Buster Sandbox Analyzer and you can now run the program that you want to analyze in Sandboxie. When a program is ran under Sandboxie, you will see the API Call Log window in BSA being filled up with information.
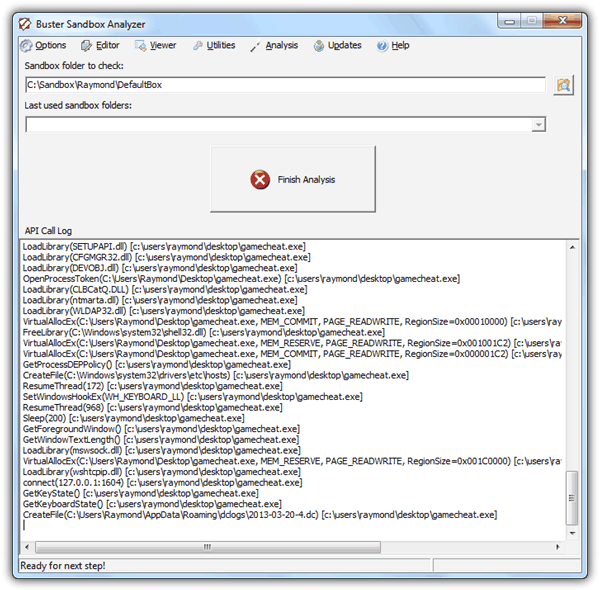
Once you’re done testing the program and want to analyze the program’s behavior, you will first need to terminate the process from the Sandboxie Control by right clicking and select “Terminate Programs”. Go back to Buster Sandbox Analyzer and click Finish Analysis button. Click on Viewer at the menu bar and select View Analysis. An analysis text file will open showing you the detailed report of the actions from the program that you ran in Sandboxie.
The screenshot below is an example of the actions created by DarkComet RAT. It checks for debuggers, task manager software presence, creating auto start in registry, logging keystrokes, privilege elevation, disabling regedit & task manager and connects to a remote hosts with port number.
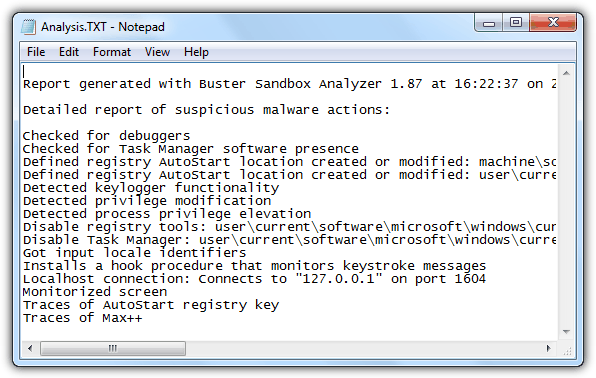
Additional Notes: Some malware has anti-debugger functionality where it automatically terminates itself when it is being ran in debugging tools or virtual machines to prevent analysis or to trick the less experienced users into thinking that the file is safe. Buster Sandbox Analyzer is certainly ahead of the game because it is updated at least once a month to prevent malware from recognizing it as a debugger.
Download Buster Sandbox Analyzer
Manual Analysis
Manually analyzing the program’s behavior from Sandboxie is possible without using any third party tools but you won’t get detailed analysis compared to using Buster Sandbox Analyzer. You can easily find out if the sandboxed application is programmed to drop any additional files to the hard drive and added any autostart values in the registry which is enough evidence to determine that the program is malicious.
To view the file changes, right click at the DefaultBox from the Sandboxie Control window and select “Explore Contents” or alternatively directly go to C:\Sandbox\[Username]\DefaultBox\. If you see any folder such as “drive” or “user”, it means that the sandboxed application has created some files in the hard drive. Continue accessing the folders until you see some files. Below is an example of a suspicious behavior where a sandboxed application ran from desktop creates another copy of itself to the current user’s application data folder.
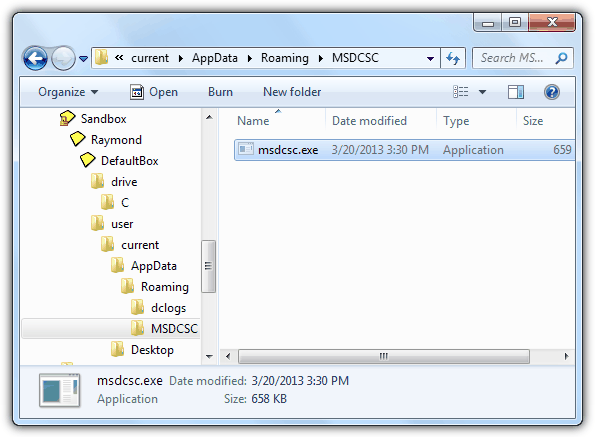
As for analyzing the registry changes, you will have to first terminate the program from Sandboxie Control. Press WIN+R to open the Run window, type regedit and click OK. Expand HKEY_USERS registry folder by double clicking on it, click File from the menubar and select Load Hive. Browse to C:\Sandbox\[UserName]\DefaultBox\ and open RegHive without any file extension. Enter anything such as sandboxie for the Key Name for easy identification and click OK.
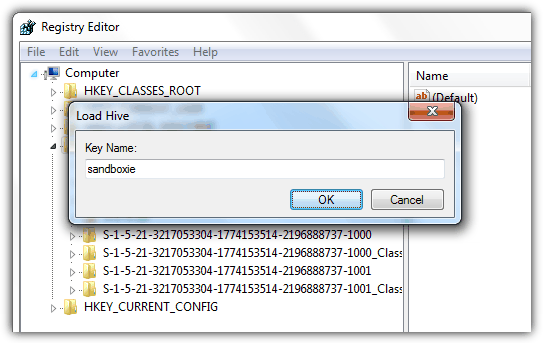
Another registry folder with the name that you’ve previously set for the Key Name will be added to the end of the HKEY_USERS. You can now expand the registry folder to analyze the values being added or changed.
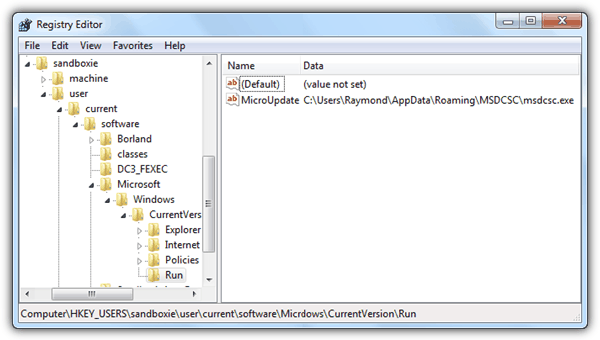
As you can see from the sample screenshot above, the sandboxed applcation in Sandboxie also added an automatic startup value to the current user in registry to run the file that was dropped to the Application Data folder when the user logs in. A computer user with experience and knowledge would be able to evaluate that the behavior of the sandboxed application is most likely malicious and you can get confirmation of your findings by sending the file to antivirus analyst using X-Ray.



User forum
7 messages