UltraVNC Password Decrypt Online: A Simple Guide

If you’re looking for a way to decrypt your UltraVNC password, you’re in the right place. Although Windows provides a remote desktop feature that does something similar, UltraVNC remains popular for its cross-platform compatibility and free use (unless you’re using premium versions of RealVNC for extra features like the deployment tool).
UltraVNC stores its encrypted password in an INI file, and there are methods to easily decrypt it online.
Locating the encrypted VNC password
Unlike most VNC software that stores encrypted passwords in the registry, UltraVNC saves it in an INI file. Here’s how you can locate the encrypted password:
- Navigate to the C:\Program Files\UltraVNC folder.
- Open the ultravnc.ini file.
- Look for passwd or passwd2. These values represent the encrypted password.
If you’re looking for passwords for other VNC variants, here are the locations:
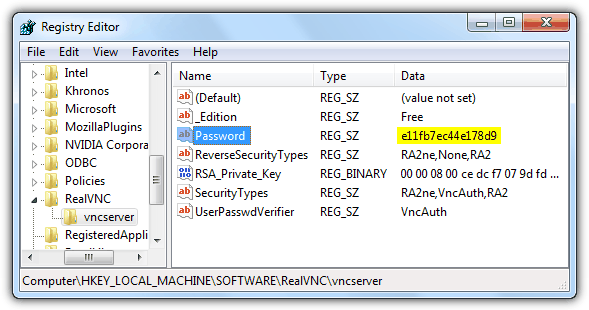
- RealVNC
HKEY_LOCAL_MACHINE\SOFTWARE\RealVNC\vncserver
Value: Password - TightVNC
HKEY_CURRENT_USER\Software\TightVNC\Server
Value: Password or PasswordViewOnly - TigerVNC
HKEY_LOCAL_USER\Software\TigerVNC\WinVNC4
Value: Password - UltraVNC
C:\Program Files\UltraVNC\ultravnc.ini
Value: passwd or passwd2
Once you’ve located the encrypted VNC password, you can proceed with decrypting it using one of the following methods.
Decrypting the encrypted VNC password
Method #1: Web-based
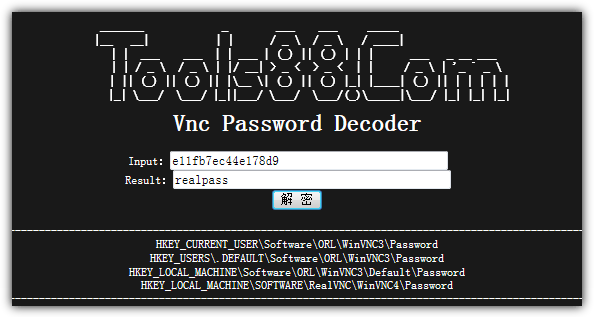
For an easy, online solution, you can use the VNC password decoder at Tools88.com. This tool has been running since 1997 and allows you to decrypt your UltraVNC password quickly.
Simply paste the encrypted password into the Input box, click the button with two Chinese characters, and the real password will be shown in the Result box.
Method #2: Command line tool
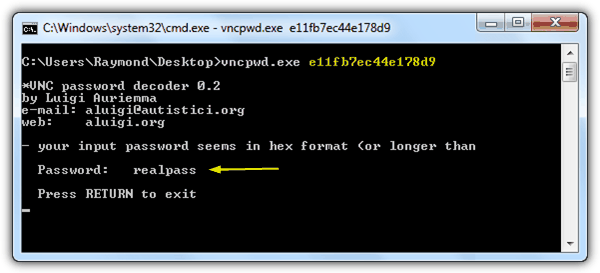
Alternatively, you can use the VNC Password Decoder (vncpwd) tool by Luigi Auriemma, which can decrypt UltraVNC’s DES encryption.
To use it, run the tool from the command line, providing the encrypted password, and the tool will reveal the actual password.
To use vncpwd, open the command prompt, navigate to the folder containing vncpwd.exe, and run:
vncpwd.exe ENCRYPTEDPASSWORD
Download VNC Password Decoder (vncpwd)
Conclusion
Recovering your UltraVNC password is a straightforward process once you locate the encrypted credentials. Whether you opt for an online decoding tool or a command-line utility, decrypting UltraVNC passwords is easier than you might think.
If you’re managing remote connections, you might also find it helpful to scan for active VNC servers on your network. For those looking for a faster way to deploy VNC, check out Fastpush, which allows silent and remote installations.
Beyond UltraVNC, security enthusiasts may also be interested in learning how to find hidden passwords in Firefox or decrypt MD5-hashed strings for additional cybersecurity insights.
If you’re troubleshooting remote access, you can also access a remote computer in just 2 minutes without port forwarding or explore various software solutions to control a computer efficiently. Additionally, for digital forensics, you may find value in parsing and analyzing Windows LNK shortcut files.



User forum
11 messages