I Tested 5 Free Online Malware Sandboxes and They’re the Easiest Way to Catch Hidden Threats
Want to test a suspicious file without risking your PC? These online sandbox malware analyzers let you upload and safely inspect files in a virtual environment—no downloads or installs needed.
While antivirus tools and online malware scanners help, they can miss freshly packed malware. That’s where sandbox analyzers come in.
Whether it’s an .exe, document, script, or browser file, you’ll get a detailed report showing what the file does, what processes it starts, and if it shows signs of malware.
Here’s a list of the best free online sandbox services you can use to analyze files safely.
Best free sandboxes to detect malware
1. Cuckoo Sandbox
Cuckoo Sandbox is open-source and one of the most advanced sandboxes you can find. You can install it locally or use online services powered by Cuckoo.
It analyzes Windows, Linux, and even Android files. Reports are detailed, showing behavior, API calls, and dropped files. There’s a learning curve, but it’s powerful once set up.
2. Jotti’s Malware Scan

Jotti focuses more on antivirus results than deep sandbox analysis, but it’s still useful. It scans files with multiple antivirus engines and highlights suspicious behavior.
You won’t get behavior reports like other sandboxes, but you’ll know if a file is flagged by popular AVs. Max upload size is 100MB.
3. Hybrid Analysis
Hybrid Analysis blends traditional sandboxing with threat intelligence. It runs your file and scores it based on risk factors like system changes, network activity, and suspicious patterns.
It works with PE files, Office docs, PDFs, and archives. You get a report with threat scores, behavior summaries, and YARA rule matches.
4. VirusTotal
VirusTotal is more than just an antivirus scanner—it also runs basic sandbox analysis (via partners like Crowdsourced YARA and Behavioral Information).
You can upload files, share URLs, and check behavior logs like file creation and registry edits. It’s not as deep as dedicated sandboxes but perfect for a quick overview.
5. Joe Sandbox Web
Joe Sandbox is advanced and customizable, but now requires a free account to access. Once you sign up, you can upload files and get deep behavior reports.
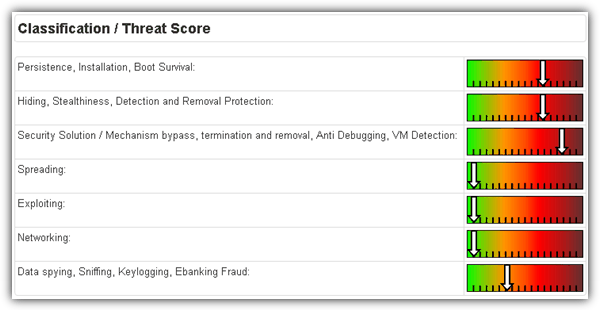
It currently supports only Windows XP in the free tier and limits users to 100 reports/month. Still, the detail level is impressive—perfect for malware analysts.
Final Tips
No single sandbox catches everything. Some malware will detect the virtual environment and stay dormant. That’s why it’s smart to run files through multiple tools. If a file behaves oddly—even if reports look clean—it’s safer to keep it off your system.
Interested in speed and IOC extraction, especially VBA/Powershell/JS/VBS/Cmd de-obfuscation? Try out filescan.io!
As for me, the best sandbox now is any.run
Limited to 16 mb exe’s. Useless if you need to test anything bigger.
So many edda links this page is now useless
For deep static malware analysis you could try MalwareAnalyser.io
Online malware anomaly-based static analyzer with heuristic detection engine powered by data mining and machine learning.
The ThreatExpert link is no good anymore. Looks like Symantec now owns them.
Very Informative!
Check this as well
sandbox.anlyz.io
thanks
I just voted . Its a small way to repay you for everything that you have written to help me and others like me! Good luck!
Judiline
thanks
thanks a lot Ray.
Thanks, Raymond. I regularly upload files for analysis by VirusTotal, NoVirusThanks, ThreatExpert and CWSandbox. I think CIMA would be an intelligent addition in my Bookmarks.
Thanks for the information.