15 Best Anti-Rootkit Tools to Remove Malware [2023 List]
There are many different types of computer malware and the ones that use rootkit technologies are the worst because they are hardest to detect and remove. Rootkit technology is able to hide its presence from the most basic tools built into Windows such as Task Manager, to your most trusted firewall or antivirus software and you won’t even know that it’s there. This is achieved through installing and loading kernel-mode drivers which can allow the malware to run with higher privileges.
Although 64-bit Windows operating systems are generally safe from rootkit infection because by default the operating system only accepts signed driver files, there were previous cases where legitimate digital certificates were stolen by hackers and used to sign rootkit drivers to bypass security software and Windows defenses. Antivirus software was not much of a help either because the Stuxnet worm successfully stayed infected on the computers for years before it was discovered by VirusBlokAda, the developer of VBA32 antivirus software.
Since antivirus software are far from being perfect in catching rootkits, we’ve put 15 dedicated anti-rootkit tools to the test and see if they are able to detect the 3 different keyloggers (All In One Keylogger, Invisible KeyLogger Stealth, Elite Keylogger) that uses rootkit technology which we have installed on our test system.
1. avast! ANTIROOTKIT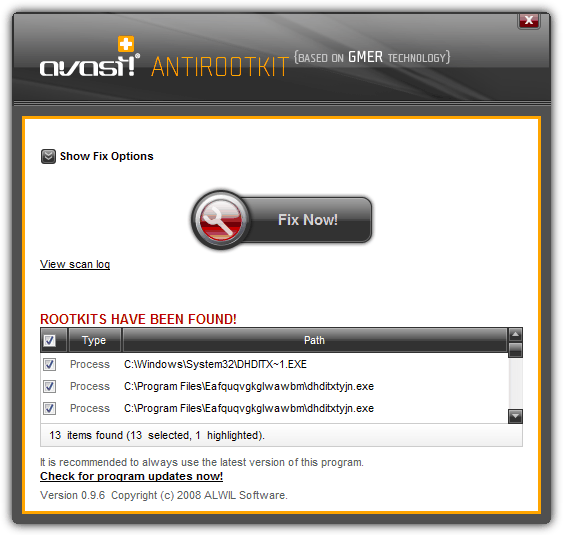
This free and portable anti rootkit tool by avast! is outdated and no longer being maintained since 2008 because it has been integrated into their antivirus program but can still be downloaded directly from their server. Using rootkit detection technology based on GMER, avast! ANTIROOTKIT only managed to detect All In One Keylogger while missing the other two driver-based rootkit keyloggers. Clicking the “Fix Now!” button successfully deleted the files after a restart.
2. AVG Anti-Rootkit
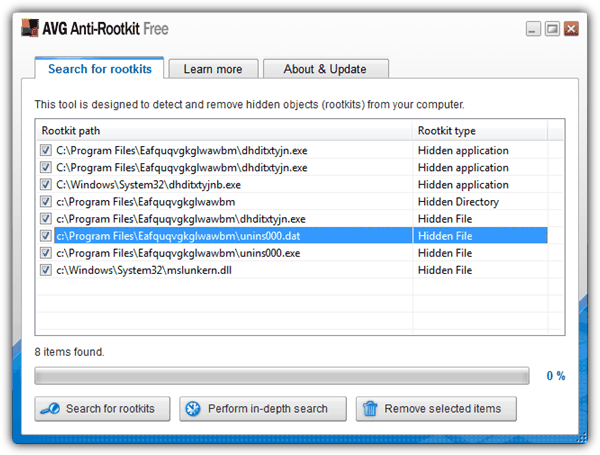
This free anti-rootkit tool by AVG suffers the same fate as avast! because it has been abandoned since 2006 due to the integration of this anti-rootkit into their antivirus software. The program requires installation, a reboot and either manually run as admin or disable UAC to run. The result of AVG Anti-Rootkit is also the same as avast! where only All In One Keylogger is detected while missing Elite Keylogger and Invisible KeyLogger Stealth. The “Remove selected items” button does not delete the infected files but replaces the last character of the file’s extension with an underscore, for example from .exe to .ex_
3. Bitdefender Removal Tool / Rootkit Remover
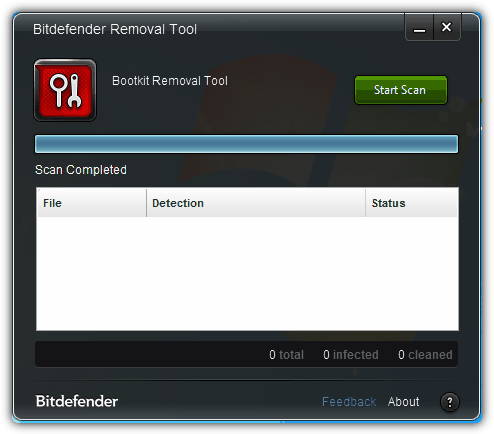
We weren’t able to determine the if Bitdefender’s antirootkit tool is called “Removal Tool” or “Rootkit Remover” because the program’s name and website says differently when they are the exact same application. Bitdefender Removal Tool is free, portable and up-to-date (last update on February 2013) but can only detect known rootkits through signatures and not the undetected ones. The scan takes merely a second to tell you if there are any rootkit threats detected. Both 32-bit and 64-bit versions available. Bitdefender Rootkit Remover fail to detect all 3 rootkit keyloggers.
Download Bitdefender Removal Tool / Rootkit Remover
4. HitmanPro
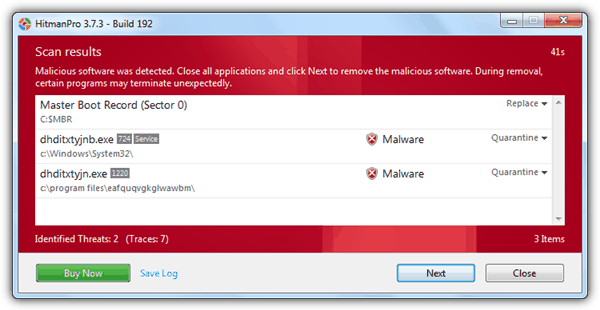
HitmanPro is a popular second opinion malware scanner that first uses behavioral analysis to determine if a file is a possible threat and then automatically uploads the file to have it scanned in the cloud with 5 different antiviruses for confirmation. Although HitmanPro is shareware, you can use it to scan your computer for free while removal is only available during the 30-days trial. All In One Keylogger was detected because Ikarus and G Data indicated that the file is malicious. HitmanPro found Elite Keylogger files to be suspicious but wasn’t flagged as a threat because none of the antiviruses detected it as malicious after the cloud scan. Invisible KeyLogger Stealth wasn’t detected at all.
5. Kaspersky TDSSKiller
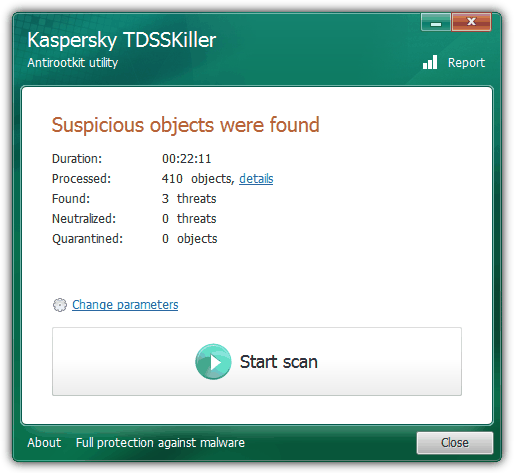
Kaspersky TDSSKiller started off as a removal tool to detect and clean up the Alureon/TDSS/TDL rootkit and has grown to recognize a few other rootkits including bootkits. Upon testing, Kaspersky TDSSKiller missed all 3 rootkit keyloggers and even wrongly detected 3 legitimate system (.SYS) files belonging to COMODO Time Machine as suspicious objects with medium risk.
6. Malwarebytes Anti-Rootkit
Malwarebytes Anti-Rootkit is the new kid on the block for detecting and removing rootkits that is still in BETA status. It received a lot of reviews and publicity when it was released to public because everyone had very high hopes for products by Malwarebytes.
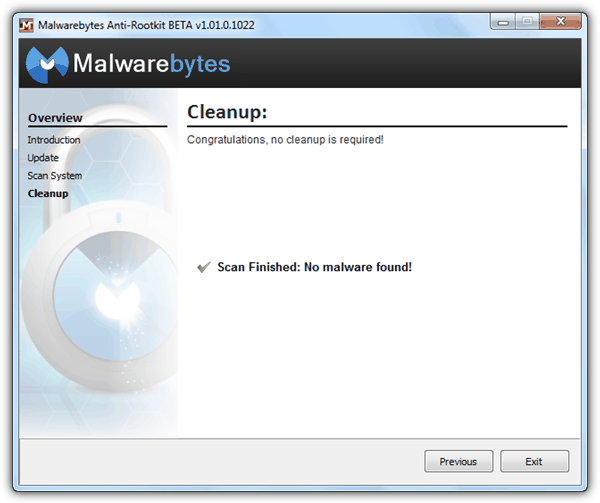
It is unclear what variants of rootkits can be detected by Malwarebytes Anti-Rootkit because it is not mentioned in their official website, but it failed to detect any of the 3 rootkit keyloggers during testing. A very useful tool called “FixDamage” that comes together in the ZIP archive file can be used to repair damages made by rootkit by restoring important Windows services.
Download Malwarebytes Anti-Rootkit
7. McAfee Rootkit Remover

McAfee Rootkit Remover is a very simple and small (532KB) utility to detect and remove ZeroAccess and TDSS family of rootkits. The program runs on command line window, automatically checks for updates and takes only a few seconds to scan for rootkit infections. As expected, McAfee Rootkit Remover didn’t detect all 3 rootkit keyloggers as threat because it can only recognize 2 types of rootkits that was mentioned earlier.
Download McAfee Rootkit Remover
8. Norton Power Eraser
We don’t normally see Symantec offering any of their tools for free. Even their rescue disk known as Norton Bootable Recovery Tool requires a valid product key to run. Thankfully there is one tool called Norton Power Eraser which is free to use for detecting and removing malware that is hidden deep inside the system.
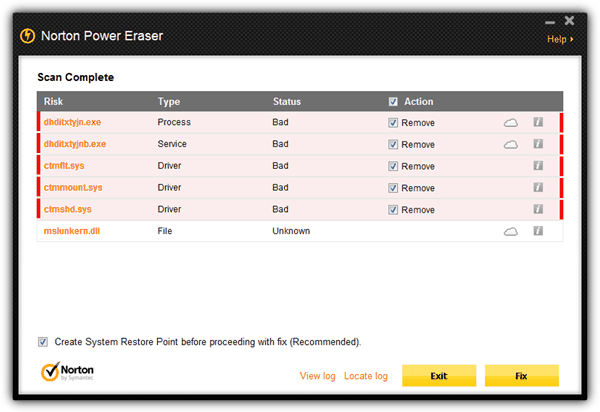
It is a single portable executable file of only around 3MB in size. The Rootkit scan option is enabled by default in Settings and will first require a restart before performing a rootkit scan. Norton Power Eraser detected All In One Keylogger and Invisible KeyLogger Stealth. As for Elite Keylogger, one of the DLL files are flagged as unknown. Other than that, it also had 3 false positives by detecting COMODO Time Machine driver files as unsafe.
9. Trend Micro RootkitBuster
RootkitBuster is a free tool by Trend Micro that is able to check multiple locations in Windows such as the Master Boot Record (MBR), files, registry entries, kernel code patches, operating system service hooks, file streams, drivers, ports, processes and services to identify rootkit presence. It was last updated a month ago and has dedicated builds for both 32-bit and 64-bit.
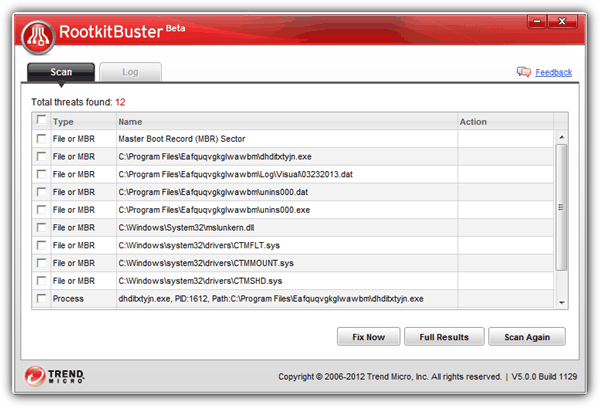
RootkitBuster only managed to detect All In One Keylogger while missing the other 2. It also has the same false detection as Kaspersky TDSSKiller and Norton Power Eraser by wrongly identifying 3 system driver files as threats.
Download Trend Micro RootkitBuster
10. UnHackMe
UnHackMe is the only shareware rootkit killer with monitoring capabilities to auto check your computer for any possible rootkit infection. The trial version of UnHackMe allows you to use it for 30 days without limitation. The program’s user interface looks simple enough for beginners to use and you can even send the generated regrunlog.txt report file to their support center to obtain advice if you’re not fully sure the detected unknown/suspicious file is indeed malicious.
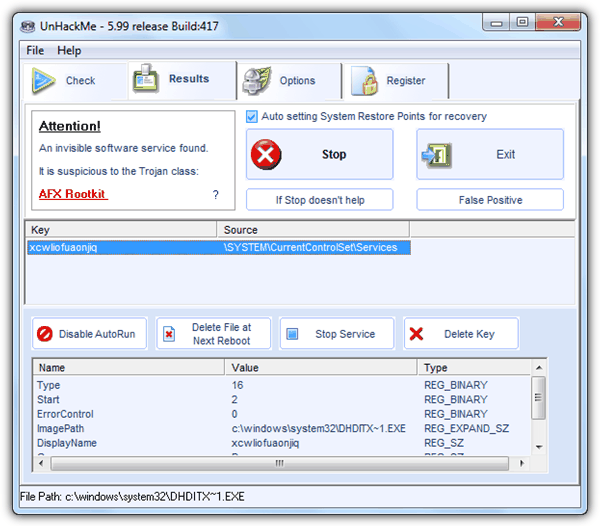
There are a few buttons such as stopping a service, deleting a registry key and disabling autorun to help disable the suspicious file but we found that most effective one is the “Delete File at Next Reboot” if the malware is very persistent. UnHackMe found All In One Keylogger and Invisible KeyLogger Stealth but missed Elite Keylogger.
As you can see from the results above, very few automated rootkit detection tools manage to detect all 3 rootkits. Norton Power Eraser did the best by confirming 2 infections with 1 unknown status. There is another category of antirootkit utilities designed for more advanced users to manually analyze, decide and remove rootkits which can be found on the next page.
Unlike the previous list of antirootkit detection tools which is meant for average computer users to automatically recognize rootkit infections and offer to remove them, the 5 free utilities below are meant for advanced users to manually analyze hidden processes, drivers, registry keys, files, startup entries, services, scheduled tasks, ring0 and ring3 hooks, etc and self determine if the items are safe or malicious. Other than using them to detect rootkits, it can also be used to find other malware such as trojan, rogueware, worms and viruses.
11. AntiSpy
AntiSpy is a new portable tool that the first version was released early 2013 and a new version has been released every month. The official website is in Chinese but the program is fully in English. Running the executable file will open up a window with a couple tabs allowing you to view both visible and hidden items.
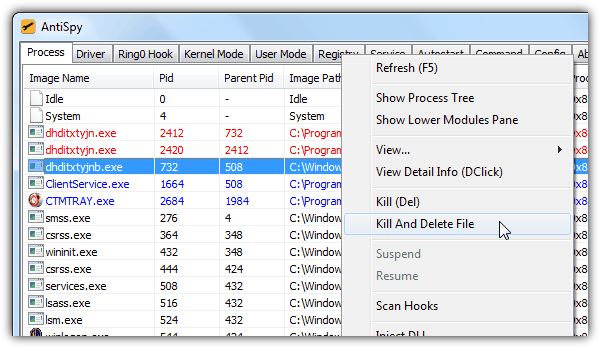
As you can see from the AntiSpy screenshot above, a process colored in red is found to be suspicious and right clicking on the item provides many options to investigate or take action such as kill and delete file. The registry, service and autostart tab is worth looking at because you are able to delete protected registry keys that cannot be done from regedit.exe, view hidden services that don’t show up in services.msc and reveal hidden items that autostart with Windows. As good as it is, AntiSpy is short of a low-level file browser to view hidden files and folders.
12. GMER
GMER has been around since 2006 and is still being actively developed today with full 64-bit support. An advantage in GMER is it will automatically start a quick scan upon running to find system modification which might have been caused by rootkit activity.
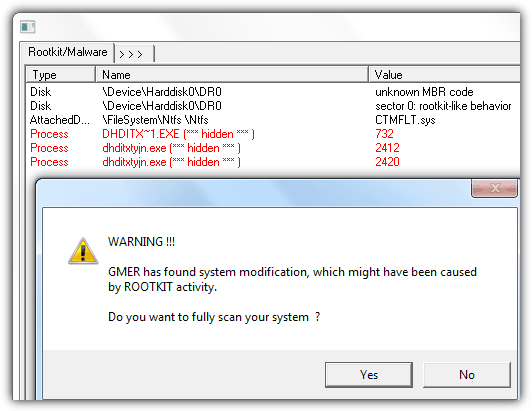
We found that GMER is more of an analyzer rather than a tool to remove antirootkits because you can only kill process but without an option to delete running processes, modules, registry keys and autostart items. The “Files” tab where you can access your files from in an Explorer-like interface also doesn’t seem to show files and folders that are hidden by rootkits.
13. NoVirusThanks Anti-Rootkit
This anti-rootkit tool by NoVirusThanks is free for non commercial use and is recommended to be used by experienced users because the program shows a lot of technical information especially code hooks although the less experienced users can still run a quick scan on the Quick Report tab to find any process that runs hidden and is labeled as suspicious. There is a “Hosts File” tab which is often ignored by most antirootkit tools to check if it has been modified by malware block security websites.
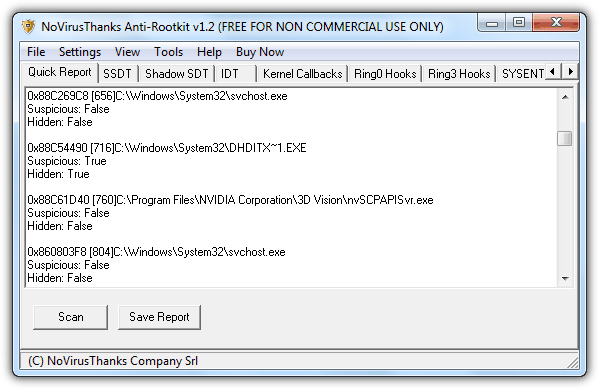
The program requires installation and works from Windows 2000 to 7 on 32-bit only.
Download NoVirusThanks Anti-Rootkit
14. PC Hunter
PC Hunter is a free anti-rootkit that is developed from XueTr (also an anti-rootkit tool) that comes in both Free and Pro version. Compare to the rest, PC Hunter seems to have the most options to view processes, kernel module, ring0 and ring3 hooks, network connections, startup info, file association, firewall rules, and even useful tools like a registry editor, file manager, safeboot repair, enable disabled registry and task manager.
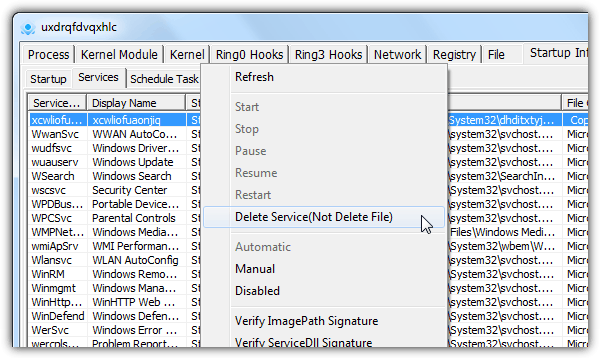
If you’re stuck with interpreting the results, it is possible to generate a report from the “Computer Examination” tab, export it to a external text file and send it to an expert to get help in identifying rootkits. PC Hunter works from Windows 2000 to 8 and even has a special 64-bit build that can be used from Windows 7 x64 onwards.
15. PowerTool
PowerTool is not just another rootkit analyzer tool because it has its own unique features. Other than viewing hidden process, kernel module, hooks, file, registry, startup items, services and network connections, some of the useful features found in PowerTool are showing the status of item that are normally disabled by malware from the System > Repair tab.
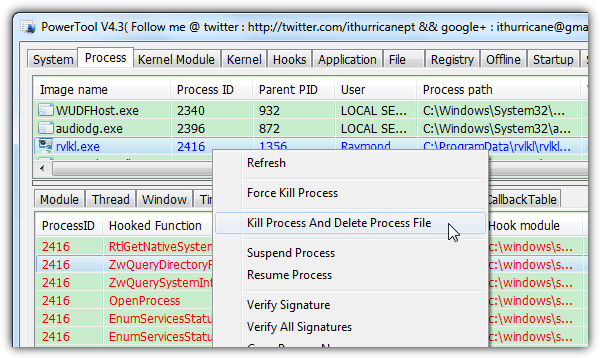
The loophole tab shows the critical patches that isn’t installed on your Windows operating system and the hardware tab analyzes the basic hardware on your computer together with the CPU, hard drive and video card temperature. The PowerTool for 32-bit is currently at version 4.3 while you should download the version 1.2 if you’re looking for the 64-bit. During testing we occasionally experienced the program crashing with a runtime error.
Additional Tests: There are some standalone offline on-demand malware scanners offered for free usage by antivirus companies that claims to detect rootkits. We’ve tested COMODO Cleaning Essentials, Dr.Web CureIt!, F-Secure Safe Easy Clean, Sophos Virus Removal Tool, VIPRE Rescue and VirIT eXplorer Lite but unfortunately none of them detected any of the 3 rootkit keyloggers installed on our test system.
Final Note: No matter how user friendly or easy it is to use the anti-rootkit tools, you must use it with care to avoid wrongly disabling an important process/driver that may cause Windows not to boot up properly. Always get advice from tech support forums or perhaps send the suspicious file to antivirus companies using X-Ray to get confirmation if the file is a rootkit.


perhaps winpatrol war. and winpatrol has a hidden folders viewer that might turn something up.
i would be curious if your samples would be visible in winpatrol. it has a tab for viewing “hidden” process etc.
Very nice and great post.thanks for sharing.
This is interesting finding, especially none of the so-called-simple tools are able to detect all of them; unless you are using the manual / advanced methods
1. Nice work. I hope you will provide n update on whether any of these tools find your three test cases 1 month and 3 months later.
2. Your original testing is critical but the reviews would be greatly enhanced by a incorporating recent results from elsewhere (e.g., how did TDSS Killer do in av-comparatives, av-test, or PC Mag)
3. As you note, some of the tested tools have not been updated in years so I don’t really see the point in testing those when you did not test several other tools that are more current.
4. I recently looked at RogueKiller. It has been around for awhile but now has a GUI. The site and documentation are in French but (slightly rough) English translations are available. RogueKiller is firmly in the advanced user camp. Some of the repairs are a bit heavy handed: options other than all or nothing are sometimes lacking.
RogueKiller checks for rootkits, rogue processes, rogue registry entries, rogue or untrusted drivers, and master boot record (MBR) modification. RogueKiller can even restore the Host file, delete Proxy entries, and repair shortcuts. Some features rely upon white and blacklists. Be _very_ careful.
Thank you verry much…
thaks
Hello Ray,
Nice article.If you remember,there was a toolkit called AVZ(sorry,I don’t have any links,it is a Russian anti-malware which was later bought by Kaspersky).
Any chance you can try this?
dind’t knew about norton anti-rootkit, i have added it to my setup
thank you raymond, great review.
Ray,could you please test emsisoft toolkit and let us know what happened with the detection?Thank you
Hi joe, I’ve tested Emsisoft Toolkit and it only found one of the rootkit through signature. Another rootkit was partially detected because only the log file was being flagged but not the driver. The official website did not state anything about detecting rootkits which is why I did not include Emsisoft Toolkit.
Thanks for this info !!
Have you heard about this new AntiRootkit Remover called: OSHI Unhooker?
Have you tested it?
Hi Icaro, yes in fact I’ve already tested OSHU Unhooker but did not include it since it is not fully automated and failed to detect all 3 rootkits.
This is a really great test Raymond. It looks to me like none of these company’s are taking root kit detection very seriously, it looks like we will have to use multiple programs to do a reliable root kit scan on our systems. I thought for sure at least a couple of them would get it right. Bit Defender and Kaspersky were a big surprise to me, I thought they would both do pretty well.
Ray Any opportunity to see how MS’s MRT or Safety Scanner does against these three would be much appreciated.I think those are two of the most overlooked,and effective free tools with root kit removal capability available to date.
hi reym,
this is manoj from india appreciate your artical everytime followed last 4 5 yrs
thanks for posting such wonderful information free
Hi,
Nice test, but you missed a lot of things here.
Which settings you used before the tests, there are the results from the scan etc.
TDSSKiller can be configured to detect unknown services
i.imgur.com/Sbf88.png
Aswar is really old. I prefer Gmer or AswMBR for bootkits.
Bitdefender created many tools for rootkits detection but they left them behind and they didn’t implemented them in one product as Kaspersky did with TDSSKiller.
HitManPro can be configured to scan with EWS
i.imgur.com/vU2W6iV.png
However you should be very careful when using HitManpro, because sometimes he can’t repair the BCD settings properly and the system will become unbootable.
You tested McAfee Rootkit Remover which is only for ZeroAccess and not McaFee Rootkit Detective?
Norton Power Eraser gives a lot of false positives.
Unhackme is not so good. The most of the time you should use RegRun Warrior CD to get the job done. Not very good for shareware.
Gmer can delete files and services…you can use batch files for that purpose.
For example:
gmer.exe -del service gasfkyeydxlkaw
gmer.exe -del reg “HKLMSYSTEMControlSet001Servicesgasfkyeydxlkaw”
gmer.exe -del file “%systemroot%system32driversgasfkyktfoqdtk.sys”
gmer.exe -del file “%systemroot%system32gasfkywsp8y.dll”
gmer.exe -del file “%systemroot%system32gasfkyyicofjwf.dat”
gmer.exe -del file “%systemroot%system32gasfkycpoyvxdq.dll”
gmer.exe -del file “%systemroot%system32gasfkyjktjolda.dat”
gmer.exe -del file “%systemroot%system32gasfkyetodsrmt.dll”
gmer.exe -del file “%systemroot%system32gasfkybgdkopjo.dll”
gmer.exe -reboot
The following products are missing as well:
Win64AST, avirarkd (Avira anti-rootkit), Vba32 AntiRootkit, SysProt, Rootkit Unhooher 3.8.388.590, RootRepeal, SanityCheck Home Edition (x64), Dr.WebCureIt (has a built in anti-rootkit), f-secure blacklight (yes it’s old but AVG anti-rootkit is old as well, so it can be included). :)
The other tools can be found here:
kernelmode.info/forum/viewtopic.php?f=11&t=10
Anyway, thank you for the test. It was interesting to read it with my coffee. :)
Keep up the good work!
Regards,
Georgi
after along time… thank you for this nice article… i am using emsisoft malware for quite sometime…what are your ratings for this one raymond…
Thanks for the update!!!
Good rule of thumb I always say, is that when you have names like dhdbiquxyt.exe, you know you have something bad in there.
Ray, have you tried Sophos Rootkit Remover? curious to see the results of the rootkits you tested.
Jim, the Sophos Rootkit Remover redirects me to their free Sophos Virus Removal Tool which failed to detect all 3 keyloggers. Check the “Additional Tests” information found on the end of the second page.
Thank you very much !
The best is UnHackMe.
Hi Raymond, I understand that GMER has been integrated with AVAST, but you can download GMER zip/exe from the GMER website and it’s being constantly updated. Is it the same one that AVAST is using or is it different? If different, could you test it out as well please?
Thanks for all the hard work! Malaysia Boleh!
Hi Mark, the guy who created GMER works for AVAST which is why the “technology” in detecting rootkits used by GMER is integrated into AVAST products.
Appreciate this article.
Thank you!
I need this software!
Great posting Raymond. Really appreciate all the hard work that has gone into this article on AntiRootkits. Sure saves me (and others) a lot of time surfing the net only to find skewed opinions! Your final note is very apt and a friendly reminder to tread with care when using these tools – as you so eloquently state “No matter how user friendly or easy it is to use the anti-rootkit tools, you must use it with care”. Your testing of various tools in this regards makes the job that much easier. Thanks again and keep up the fantastic work on this site…
Useful test Ray, very useful.
Thanks a bunch Ray!
A very useful posting Raymond – Thank you.
Appreciate this article. Thanks!
Now that is a really good post Ray!
I love the post in which you test a software for us!
I guess in November you tested all the antivirus to find out the best and you said Avira is the best free antivirus so I switched to that!
Thanks.
As usual great test from Ray.
thanks raymond
good info
Nice article, thanks for giving us links for many Antirootkits, it will be good for us, to keep at least one of these products in our computer and USB. Thanks,,,,,,,,