15 Best Anti-Rootkit Tools to Remove Malware [2023 List]

Unlike the previous list of antirootkit detection tools which is meant for average computer users to automatically recognize rootkit infections and offer to remove them, the 5 free utilities below are meant for advanced users to manually analyze hidden processes, drivers, registry keys, files, startup entries, services, scheduled tasks, ring0 and ring3 hooks, etc and self determine if the items are safe or malicious. Other than using them to detect rootkits, it can also be used to find other malware such as trojan, rogueware, worms and viruses.
11. AntiSpy
AntiSpy is a new portable tool that the first version was released early 2013 and a new version has been released every month. The official website is in Chinese but the program is fully in English. Running the executable file will open up a window with a couple tabs allowing you to view both visible and hidden items.
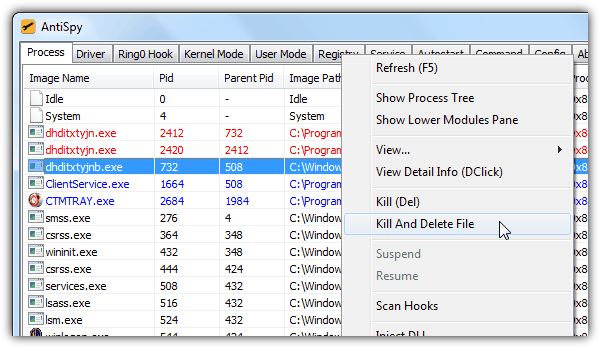
As you can see from the AntiSpy screenshot above, a process colored in red is found to be suspicious and right clicking on the item provides many options to investigate or take action such as kill and delete file. The registry, service and autostart tab is worth looking at because you are able to delete protected registry keys that cannot be done from regedit.exe, view hidden services that don’t show up in services.msc and reveal hidden items that autostart with Windows. As good as it is, AntiSpy is short of a low-level file browser to view hidden files and folders.
12. GMER
GMER has been around since 2006 and is still being actively developed today with full 64-bit support. An advantage in GMER is it will automatically start a quick scan upon running to find system modification which might have been caused by rootkit activity.
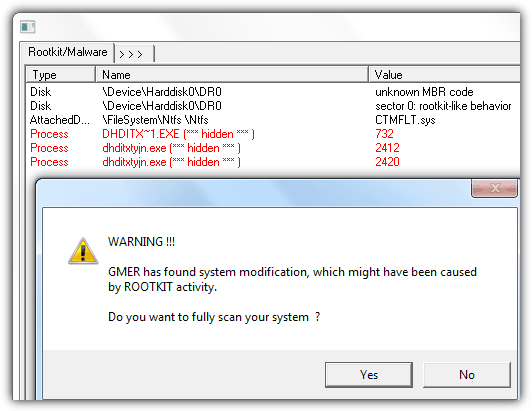
We found that GMER is more of an analyzer rather than a tool to remove antirootkits because you can only kill process but without an option to delete running processes, modules, registry keys and autostart items. The “Files” tab where you can access your files from in an Explorer-like interface also doesn’t seem to show files and folders that are hidden by rootkits.
13. NoVirusThanks Anti-Rootkit
This anti-rootkit tool by NoVirusThanks is free for non commercial use and is recommended to be used by experienced users because the program shows a lot of technical information especially code hooks although the less experienced users can still run a quick scan on the Quick Report tab to find any process that runs hidden and is labeled as suspicious. There is a “Hosts File” tab which is often ignored by most antirootkit tools to check if it has been modified by malware block security websites.
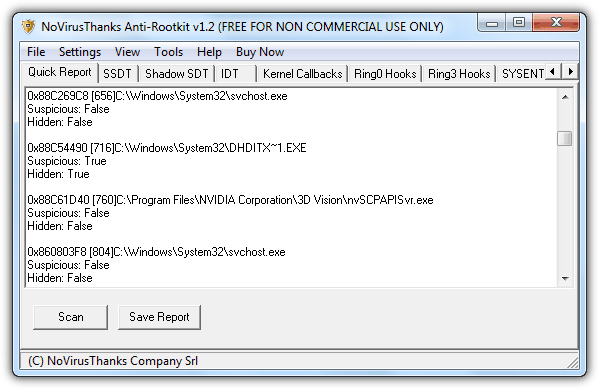
The program requires installation and works from Windows 2000 to 7 on 32-bit only.
Download NoVirusThanks Anti-Rootkit
14. PC Hunter
PC Hunter is a free anti-rootkit that is developed from XueTr (also an anti-rootkit tool) that comes in both Free and Pro version. Compare to the rest, PC Hunter seems to have the most options to view processes, kernel module, ring0 and ring3 hooks, network connections, startup info, file association, firewall rules, and even useful tools like a registry editor, file manager, safeboot repair, enable disabled registry and task manager.
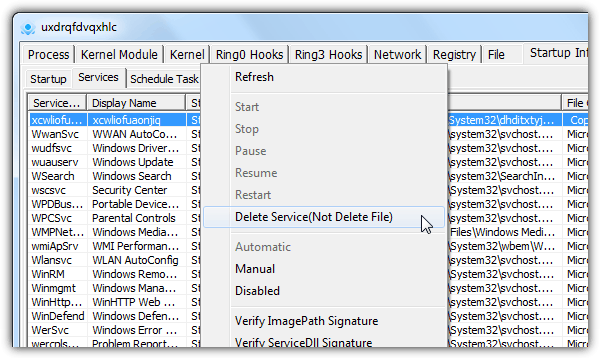
If you’re stuck with interpreting the results, it is possible to generate a report from the “Computer Examination” tab, export it to a external text file and send it to an expert to get help in identifying rootkits. PC Hunter works from Windows 2000 to 8 and even has a special 64-bit build that can be used from Windows 7 x64 onwards.
15. PowerTool
PowerTool is not just another rootkit analyzer tool because it has its own unique features. Other than viewing hidden process, kernel module, hooks, file, registry, startup items, services and network connections, some of the useful features found in PowerTool are showing the status of item that are normally disabled by malware from the System > Repair tab.
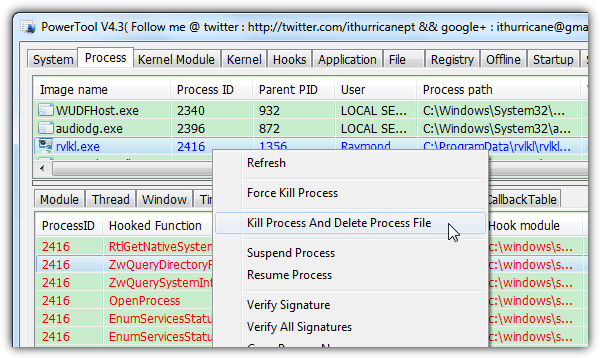
The loophole tab shows the critical patches that isn’t installed on your Windows operating system and the hardware tab analyzes the basic hardware on your computer together with the CPU, hard drive and video card temperature. The PowerTool for 32-bit is currently at version 4.3 while you should download the version 1.2 if you’re looking for the 64-bit. During testing we occasionally experienced the program crashing with a runtime error.
Additional Tests: There are some standalone offline on-demand malware scanners offered for free usage by antivirus companies that claims to detect rootkits. We’ve tested COMODO Cleaning Essentials, Dr.Web CureIt!, F-Secure Safe Easy Clean, Sophos Virus Removal Tool, VIPRE Rescue and VirIT eXplorer Lite but unfortunately none of them detected any of the 3 rootkit keyloggers installed on our test system.
Final Note: No matter how user friendly or easy it is to use the anti-rootkit tools, you must use it with care to avoid wrongly disabling an important process/driver that may cause Windows not to boot up properly. Always get advice from tech support forums or perhaps send the suspicious file to antivirus companies using X-Ray to get confirmation if the file is a rootkit.



User forum
34 messages